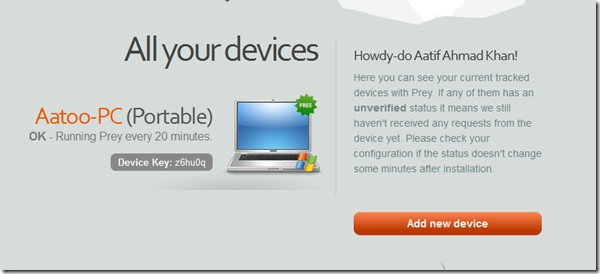
Track And Find Your Stolen Laptop With Prey
It is always a pain to lose something, both financially and in terms of the emotional stress that a person goes through. And if it is something as valuable as a laptop, which contains your personal data, the damage becomes even more pronounced. Laptops come these days with Kensington lock slots, but you cannot find a Kensington lock everywhere as well. So what is the solution?
Prey is a lightweight application that will assist you in finding a misplaced laptop should it get stolen. It is open source, multiplatform and totally free to use.
The idea behind Prey is quite straightforward. The software runs silently in background, wakes up at regular intervals and checks a particular URL to see if it should trigger the missing state, gather traces and send out a report. In checking the URL, the software looks for a 200 response from the page. If the response is there, the software goes to sleep again.
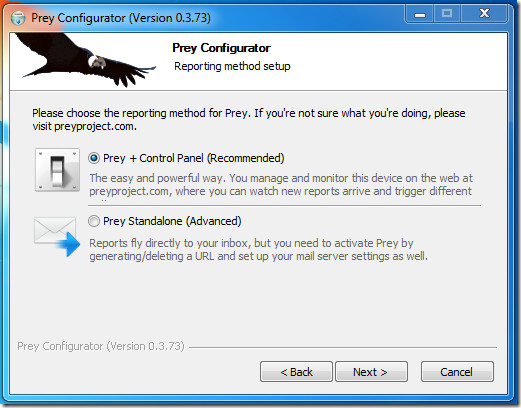
There are two approaches to using Prey. You can either have Prey+Control Panel, where you manage configuration and device state through a web page, and all of Prey’s are sent to this page. This is the easier, generally recommended approach.
The second option is to use Prey Standalone, where the reports go directly do your inbox, and in case of a missing laptop you have to generate the URL manually that will trigger Prey’s alarms. You will also need to configure the various modules yourself. This is the ‘advanced’ approach.
Naturally, Prey needs an active internet connection at all times to work. If the connection is missing, the software will silently attempt to connect to the first available WiFi hotspot and raise the alarm.
Configuring Prey is not difficult at all When you run it for the first time, the configurator will prompt you to configure device for first use.
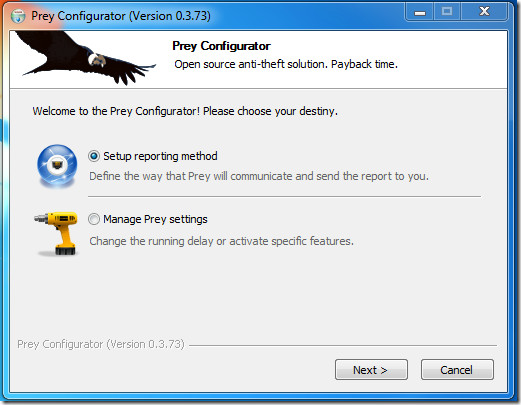
In setting up the reporting method, first thing you encounter is choosing between the two usage modes. Select your preference and go on.
Next, you will need to create an account, or sign in if you already have one for accessing Prey through the web.
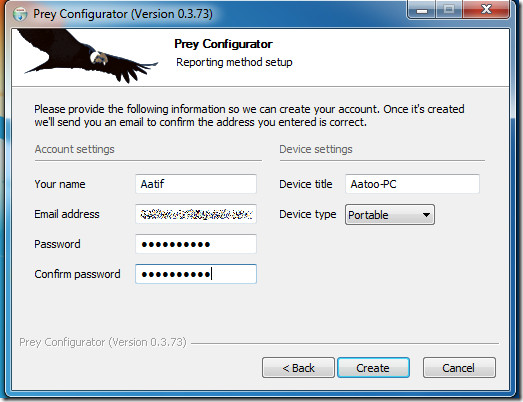
Upon creation of account, you will get an activation email in your inbox. Once account is activated, you can use Prey by logging in at www.preyproject.com. The web interface lets you control triggers for your device, the actions performed etc.
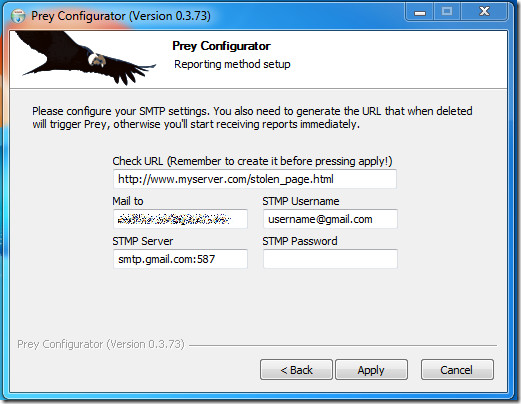
If you had chosen to run Prey as a standalone file, then you need to define the email settings for Prey to send its regular reports.
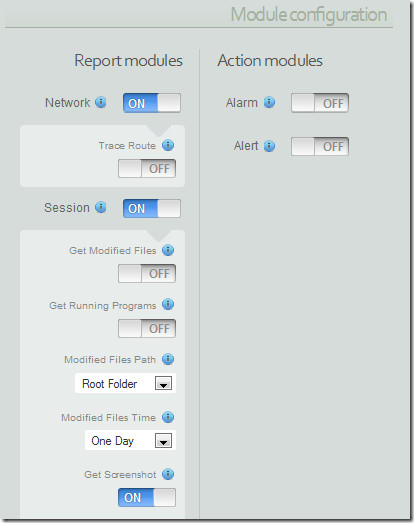
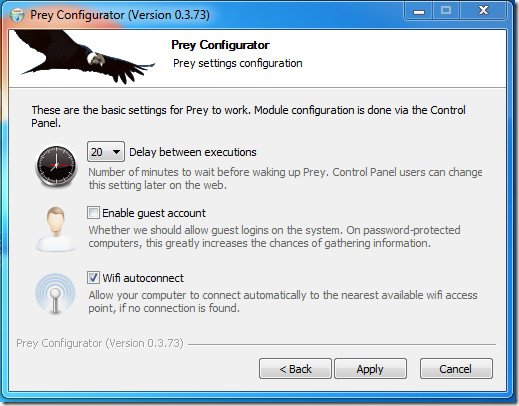
Other than that, you can also control some other features of the program by selecting Manage Prey Settings in Prey Configurator dialog. Options offered are shown below.
With all the settings in place, Prey works unobtrusively and will keep the system traceable in theft events. The software offers quite a few features, including:
- Geo-location Aware (New feature)
- WiFi auto-connect
- Lightweight
- Modula Architecture
- Powerful Report System
- Messaging/Alert System
- Full Auto Updater
Prey is multiplatform, which means it would work with all operating systems, including Windows (all versions), Linux, Mac OS X. It runs discretely hence I was not able to verify its memory signature, but the software barely leaves any effects on a system. We tested Prey on Windows 7 32-bit OS.

Why do you have a suspicious looking envelope, requiring one to click on it, to open?
Is this a trap for an illiterate computer users.
I ignored it completely! Probably contains a virus, trojan or whatever. . . .
I suggest if you want to show a message – be upfront and don’t try and sneak it into the computer. Thank you.