SecurStick – Encrypt USB stick data without administrator privileges
Data encryption tools like TrueCrypt, BestCrypt or FreeOTFE are perfectly well suited for encryption of USB drives or putting encrypted container files on USB sticks. Unfortunately, this does not guarantee a safe and completely portable storage facility. The problem lies with the necessary evil of a driver that needs to be installed in order to mount the encrypted files (or partitions) on the system. If one does not have administrator privileges on the operating system, the only way to be able to use an encrypted volume is to ask an administrator to pre-install the software… on every single computer you might just want to use your encrypted data. Well, not anymore.
With exactly this in mind, Matthias Withopf created a tool called SecurStick, an encryption program that uses an intuitive work-around that still offers you tight encryption, the ease of use by offering a virtual drive for all these encrypted files just like the programs above, but with the advantage of being able to use it on any machine (Windows, Linux or Mac) without having administrator privileges. The trick is extremely simple, yet all the more brilliant: instead of using a driver to set up a virtual drive, the program acts as a WebDAV server and maps its WebDAV location to a drive letter (which is an integrated feature of Windows and does not require administrator privileges). Well there you have it, simply perfect.
Or is it? The first thing that came to this extremely educated mind was that my WebDAV experiences weren’t that brilliant because of its speed issues. Unfortunately there’s no exception here. If it would take you about 4 seconds to copy a file to a USB stick unencrypted, then this might take you as long as 14 seconds, or more… That’s extremely slow, and one will never find such a performance decrease when using any of the encryption solutions mentioned earlier. For most types of documents this will not be a problem, but running programs that contain sensitive data via this system will probably be extremely irritating for most people. There is a known problem with WebDAV support in Windows 7, though, which is the platform I tested SecurStick on. For more information, see this forum topic.
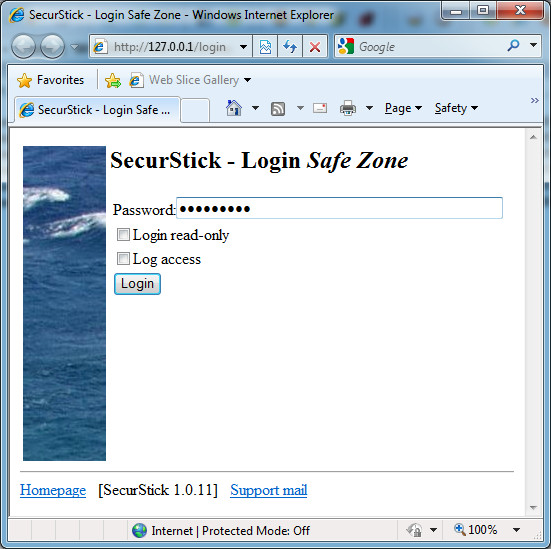
The installation is straight-forward, just extract the program to your USB drive and run it. The fact that it has a web interface does feel a bit strange at first, but one can get easily accustomed to that. After you have set up a password (for which you have to meet some extreme requirements, I think), a safe zone is created in the folder encrdata on the drive (having both “hidden” and “system” attributes). Inside, a folder called data will contain all the encrypted files; the filenames will be scrambled, if one chooses to. However, there is still some transparency from the outside as to what’s in your safe zone. The files, their sizes (when encrypted slightly bigger than the originals) and the folder structure remains visible to those who peek a bit further than most. This might not be much of a problem, and it most certainly will not let them have access to the actual data, but some degree of transparency is certainly there. What’s more, individual files can be removed by any other person in this way. Of course you have a similar risk with USB drives being formatted or encrypted container files being removed.
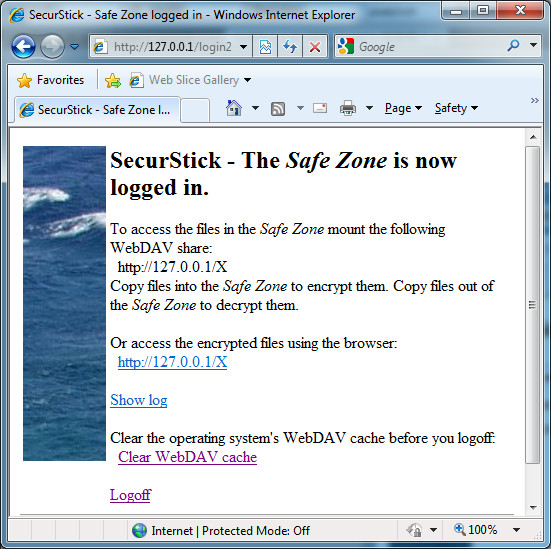
Then another potential problem popped up. “Didn’t WebDAV cache its files locally, unencrypted?” Well, the answer to my question was presented once I logged in: an HTML page with some info on the safe zone provided me with a link to flush the OS’s WebDAV cache. An extra step not to be forgotten, or you’ll leave traces of your precious files on the system. You might even have to do it several times, as some files are cached in memory as well (usually no more than about 30 seconds, according to Withopf). Again, not a problem when merely considering the possibility of your USB stick being stolen, but it does allow for an unfortunate situation in which someone finds some of your files on a computer you’ve been working on before, unencrypted… (The path for this cache in Windows Vista/7 is C:\Windows\ServiceProfiles\LocalService\AppData\Local\Temp\TfsStore\Tfs_DAV)
Whereas the concept of SecurStick is simply terrific, the method comes with quite a few downsides. But even though speed, a lack of total masking and a far-from-optimal user interface seem like a pain in the ass at first, I can seriously imagine that to lots of people this might just be the solution they were looking for.
Pros
- Finally no need for administrator privileges or pre-installed software!
- Easy to set up
- Support for Windows (x86/x64), Linux and Mac
Cons
- Transfer speed is extremely low
- File system structure transparent to outside users (to some extent)
- Possibility for outsiders to delete files
- Don’t forget to clean the WebDAV cache afterwards or you’ll leave traces of your files on the system!
Download SecurStick [via Caschy’s blog]

Sorry, but I disagree with some of your conclusions.
You write:
Possibility for outsiders to delete files
That’s the case with ANY encrypted files – even worse, with a container (like Truecrypt), once someone has deleted the container – everything is gone at once. So how is Securstick different (or worse) from any other encryption method in that case?
You write:
File system structure transparent to outside users (to some extent)
When I look at that file structure in “encrdata”, I can’t see anything. And again, IMHO the file based encryption has one huge advantage over container based encryption: If anything goes wrong, the reast is still readable. But you lose 1 byte of your truecrypt container – all your data is gone.
Which brings me to the last point: Securstick is IMHO IDEAL for cross platform cloud-based syncing / backup (with e.g. Dropbox, JungleDisk, Strato HiDrive etc.). I had looked for an alternative to EncFS (which only runs under Linux and halfbaked under Mac OSX) and SecurStick is it. You have transparent access to all your files once logged in, it runs under Linux, Mac and Windows, and you have secure, open-source file based encryption that doesn’t rely on privacy promises of your provider. And again: If one byte of your truecrypt container on e.g. Dropbox goes missing, everything is gone.