Share Your PC’s Screen With Any Computer Over WiFi Or LAN Using ScreenTask
I usually prefer services and apps on the web that are free from complex sign up procedures or complicated installation setups. Unfortunately, many screen sharing apps available for Windows suffer from both these annoyances, on top of being fairly expensive. ScreenTask is an open-source screen sharing application that simplifies this task for users who just want to share their screens with others on their local network. As the sharing is done over local WiFi or LAN, it eliminates the need for cumbersome signups. Once the app is up and running, it provides you with a unique URL that can be shared with as many local computers as you want. What’s more, ScreenTask doesn’t require client-side installation. That is, using the URL you shared with them, other users can view your PC’s screen on any web browser and any platform without additional software. Details to be followed.
The application is very easy to set up. The only quirk – if this qualifies as one – is that the app isn’t portable, so if you constantly shift between computers or networks, you can’t simply run it from a flash drive. You’ll have to install it on the system you intend to use for screen sharing. Once you’ve done that, the rest can be configured within a few mouse clicks.
Launch the application and start by selecting the network device you’re currently using from the IP drop down menu. Next, you need to specify the port number, and refresh time in milliseconds.
Optionally, you can also make the screen sharing session private with a username and password. To do that, simply enable ‘Private Task’ and fill the empty ‘User’ and ‘Password’ fields to its right. When you’re done, click the ‘Start Server’ button to begin the screen sharing session.
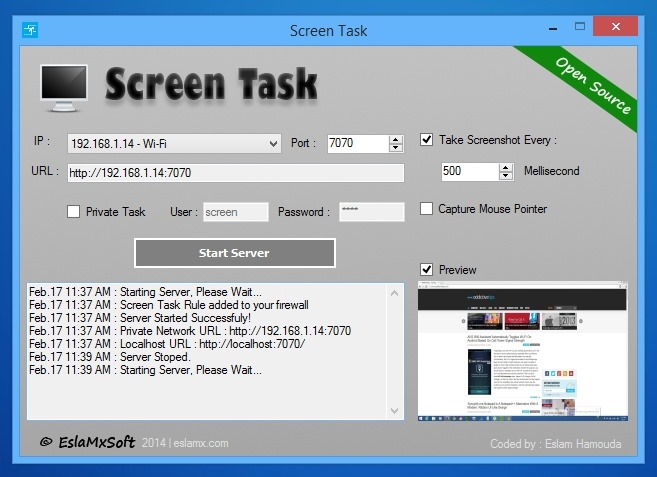
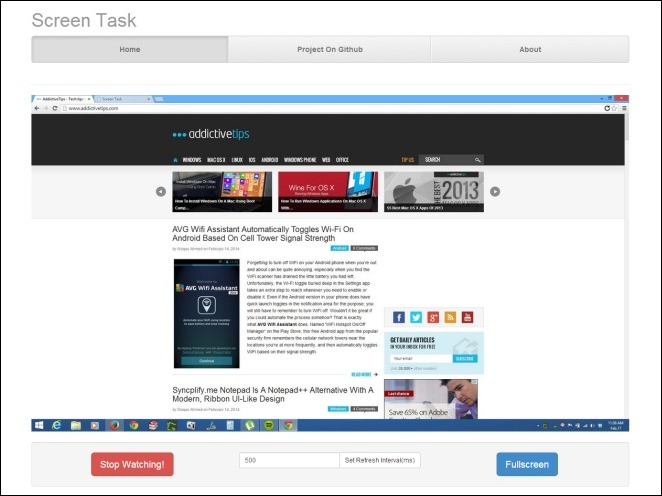
Screen Task then generates the appropriate URL for you, which you may share with others on the same network. The link comprises your PC’s IP address and the port number that was set. Recipients just have to enter the URL in the address bar of their web browsers. If the sharing session is private, they will have to enter the associated username and password.
The web-based interface has three options at the bottom that allow recipients to stop watching the session, tweak the refresh time and switch to full-screen mode.
Even though there are quite a lot of screen sharing desktop apps, if you ever find the need to share your screen with several users on the same WiFi network or LAN, ScreenTask is definitely worth trying out.

Hi Eslam,
great peace of sofware. Thank you!
I have a feature request if it is possible to implement: I have a 3 monitor setup (extended desktop) and would like to select which monitor to stream.
Tnx, Igor
Do we have an Ubuntu version of ScreenTask?
I’d recommend the developer to end the refresh rate option, its pointless. make it full screen easy comfortable and functional view to enjoy complete screen on mobile or in another browser. it just need some improvements although its nice effort needs to be appreciated. I hope to get updated version in google search results soon. good luck
i want to share my pc screen to my android over wifi …. can i use this program to get my requirements >?
Thanks my bro… you save my life because my boss asked about how to share his screen to his audience without projector lamp.
I didn’t download this software as i think there are preferable alternatives.
I just thought I’d post in reference to reading all of the comments section. Specifically, the exchange between Eslam, Gregg, nice and useful. Then between Gregg and Joe, which starts off on the up, but devolves towards the end into chest beating.
(I realize this is a useless comment, but it relieves that urge to say “I was here, this happened, someone from the future read what was typed 3 years ago”)
What are your alternatives? Are they free and faster?
Thanks in advance
Another person from the future
Well if you’re using windows, it already has the functionality built in: Remote Desktop Connection.
Also I’ve used Chrome Remote Desktop and that has worked well.
Skype has a way to share a screen.
Otherwise a quick Google search should yield the usual professional software most all of which seem to have a free version for personal use:
GoToMeeting, Teamviewer, Screenleap
Dear Eslam … i am network administrator and mostly i searched for software that use for surveillance the students during lab use. your software is very much useful when i need to look at the display screen of the student but i have one issue regarding this. that it must have the option of hide or background processing so that client or targeted user can not close this application by himself. if you made that change please inform me @ … asif.charan@gmail.com
Since the owner of this appreciated for advice, i know why some people do try to make noise.
Yes, openly,. I’m not an IT professional.
I’m just a psychologist and all i want to mention those guys is ”people making our earth heavier. Plus,. making noisy on public is an environmental issue”
Craziness can be cured by medical terms.
Stupidity cannot be cured by medical terms.
Hi Eslam,
What is the status of your application now??? Are the issues resolved with anti-virus?
Thanks.
There were never issues with his software. The issue purely lies with crap anti-virus and false positives.
Is there a limit to how many could view this shared page at the same time?
How many people/devices can view the shared screen at the same time?
This is detected as Virus by antivirus software.
Avast and Malwarebytes both find suspicious files in the installer. Is there another source for this that is clean?
I’m The Creator of this application , and i definitely grantee that there are NO Suspicious Files in the installer (you could check the source code too) Or use the ZIP Archive and scan the files , this might be because i used the SFX installer of WinRAR without signing the exe file , and when you run the application as administrator you find Publisher : Unknown , Trust me you are safe 🙂
I have tried both the Zip and The EXE file, they both flag as containing
Win32-Evo-Gen. Sorry, but your assurances are trumped by my anti-virus. I will be happy to try again once you post a clean version of your file.
TO: Eslam Harmouda
There’s pushing 40 years of my being an IT professional, with no small amount of security expertise, here, so please pay heed.
Whenever a product is flagged by Anti-Virus software, the worst and last thing that its dev should do is deny, and say it’s a false positive, and insist that there’s nothing wrong and that him/her and his/her software should be trusted. The stakes, now, are just too high for the end-user to do that.
Anti-malware software flags files and apps for a REASON. The job of the dev, when s/he’s notified of such flagging, is to figure out why it’s happening. If it’s true that there’s nothing actually bad in a file or app, it’s usually because the dev used an IDE, or pre-packed code and/or modules, which malware writers have also used; and so the precise way that said IDE formats or otherwise does things, or the presence of said code, becomes part of anti-malware databases.
When one anti-malware package flags, that’s one thing; but when two or more flag, then there’s definitely something wrong. Your software may very well be trustable, but you need to treat the fact that it’s being flagged by anti-malware products the exact same as if your app contained a bug.
Please do not insult the intelligence of end-users who’ve made thoughtful decisions about which anti-malware to use; and who then TRUST it to keep them from allowing bad things on their machines. For some reason, that anti-malware isn’t trusting you. Every con artist on punk on the planet insists on being trusted even when others say it’s a bad idea. All you do when you write such as what you’ve here written is make yourself look bad and unprofessional.
Be a professional. Fix the problem. Don’t insist that none exists.
We’ll all still be here, still happy to try your software, once you have.
Until then, please stop asking people to ignore the very tools they’ve chosen to trust. Please.
__________________________________
Gregg L. DesElms
Napa, California USA
gregg at greggdeselms dot com
Veritas nihil veretur nisi abscondi.
Veritas nimium altercando amittitur.
Thank you very very much for your precious advice , i will do my best to fix this 🙂
i have got the idea of your point as i was never thinking of it that way , but you put me on the right way of thinking , Thanks in advance.
Yours,
Eslam
Kudos on taking the advice! Too many programmers would just dig in their heels – and their projects die as a result. Hope it’s an easy fix, this looks like a great tool!
P.S. If you can manage a Portable version, that’d be exceptionally helpful.
There is actually a portable version in the download link , you can find it as ZIP Archive , extract it and use it everywhere that have the .NET Framework 4.5 installed 🙂
One could argue (and I’m not trying to make it “let’s pound on Eslam day,” here; but you’ve now brought-up an often-argued point) that if any app requires a runtime installed on the computer (be it .NET, or even Java), then it’s not really “portable.”
Technically, “portable” means that the program will run from a thumb or flash drive all by itself, relying (nor leaving any trail of itself behind) on the host computer. Personally, I subscribe to that definition…
…though I understand the counter argument that there is nary a Windows computer on the planet which doesn’t have the .NET frameword installed on it. And for that reason, I have a few portabble apps that are just so good that I’m willing to ignore that they are, at least in my opinion, not REALLY portable… at least not technically; and then I rely on the host machine’s copy of the .NET framework to make it run. At least it’s portable in its being both self-contained, and (hopefully) not leaving any registry entries or temp files.
Your app, Eslam, to be clear (just in case it seemed like I was really raggin’ on ya’ in my previous posting) looks wonderful; and the portable version of which I’d want, indeed, on the 128GB, multi-bootable, got-everything-I-need-to-fix-someone’s-computer-on-it flash drive on my keychain. But, of course, I’d first need to see that people aren’t reporting that it’s possibly malware! Maybe I’ll download the portable version and see what my anti-malware says about it; and report back here.
I wasn’t saying that you haven’t done good work, Eslam. I was simply counseling you — yes, sternly — to not put any of the problems back onto the end-user; and to suck it up and be a pro and bygod make the software work withhout a hitch without sharing with the world all the excuses.
Sometimes when I counsel that, the response is that the software is freeware, or open source, and so the user should just be happy that it exists and doesn’t cost ’em anything (in other words, “hey… it’ free… you didn’t pay anything for it… so just shut-up and accept whatever you get!”). But that, too, is the wrong (and a particularly repugnant, as well, I might add) attitude for a programmer — any programmer, whether or not working for a fee — to have. Whether the software is written for money, or for the benefit of the world, it should be done with the same amount of care and professionalism. Anything worth doing is worth doing RIGHT! And if the programmer’s name is on it, then s/he should especially care how it’s perceived, and how well it works, etc. If the programmer doesn’t feel adequately compensated, and so resents end-users complaints, then the programmer’s, first and foremost, quite likely in the wrong line of work; and/or should start charging for his/her work. It is never the end-user’s fault that the programmer decided to give away his services, and then doesn’t later feel like it was worth it. That’s on the programmer, who must be the same professional in either case.
Or so, at least, it is my two cents worth…
…which my ex-wife will be happy to attest is usually ALL it’s worth, [grin]
I look forward to the revised version of your software; and to everyone here reporting that it’s no longer tripping anti-malware.
You should expand the app to include over-the-internet control. With one of the big players in that world (LogMeIn) haviing recenttly gone entirely commercial, and the other big player (TeamViewer) nagging on every program closure to ensure that it’s being used non-commercially (and then charging outrageous prices for commercial versions); and with most of the other players in that world pretty much not really very good…
…I would think that your app, were it also capable of doing what TeamViewer does, could become kind of that hill…
…especially with how well it appears to do just the over-a-LAN part.
Just thinkin’ out loud.
Good luck to you, Eslam.
Peace.
__________________________________
Gregg L. DesElms
Napa, California USA
gregg at greggdeselms dot com
Veritas nihil veretur nisi abscondi.
Veritas nimium altercando amittitur.
You probably “technically” also tell people its a URI, not a URL!!!!
(please stay with my slightly off-topic rant, it is specifically formulated to show the triviality of nitpicking on everything and anything)
All URLs are URIs but not all URIs are URLs! That is why the distinction exists! RFC 3986 does specify that technical documentation should always refer to both URNs and URLs as URIs but if you are at a level where you read RFCs you’ll be able to identify a URN or a URL as such even though someone calls it a URI. RFC 3986 does not specify that URL is incorrect and it also does not address colloquialism, it addresses “TECHNICAL DOCUMENTATION” Why act as though everyone in the world is an IT Tech involved in TECHNICAL DOCUMENTATION? For the general internet user URL makes a lot more sense, and there is no need to correct them because their use of URL is probably 100% technically correct!
“Technically, “portable” means that the program will run from a thumb or flash drive all by itself, relying (nor leaving any trail of itself behind) on the host computer.” In other words only Linux on a bootable flash drive counts!
For everything else the OS is the “runtime” No? Thus almost nothing is portable!
Or could you more technically define what you mean by host computer. Is the hardware technically defined as the host computer or is the OS technically defined as the host computer? Perhaps your technical exposition on this question may prove that you re not an essay troll as opposed to the twitter troll you despise so much.
“Or so, at least, it is my two cents worth……which my ex-wife will be happy to attest is usually ALL it’s worth, ” ie. “even my ex-wife will attest that I am a troll”
Sorry for the late reply, but you’re an ahole….
A little wordy, but excellent points. I’m forever running into End-Users who’ve been disrespected by IT or programmers.
In all fairness, when I write a program, it’s far more important to get it functional. But it’s important to test it as a User, and it’s often hard to change hats, forget that you know anything about the program, and look at it from that perspective. Thank goodness I have people who will call me on my arrogance when it crops up! 🙂
This Made My Day, Another Precious Advice in the same hour!
Thanks in Advance for your words 🙂
You are clueless. With your “40 years og being an IT professional”, you don’t even understand how antivirus heuristics work. Sad.
TO: joe_ron
Your hateful-just-for-its-sake type — the very essence of what people mean when they use the word “troll” — always have what only they consider to be clever one-liners; but always without specifics. If you have a point, then abandon your youthfully ignorant belief in that the world may be covered in 140 characters or less, and both make said with provable facts, not not-as-clever-as-you-think, one-liner trolling.
The heuristics part of what anti-malware software which even claims to do it (not all such software does; and only a tiny handful of that which claims to can actually do it even remotely reasonably well), and virus signature database matching are two entirely-different things. No part of anything I wrote had anything to do with “antivirus heuristics.”
The very first thing for any dev of any app which is being flagged by anti-malware software is to do the easy thing first: to find out what it was about his/her files that raised the hackles of the anti-malware software; and, statistically, the vast majority of the time it’s because of a match to a signature in the database. And that’s a good thing, because once which signature is figured out, then it’s really easy to find it in one’s own software, and then remove it.
Another possibility that’s also easy to first find, and then fix, is a rules-related reason, precisely as what Eslam described wherein the problem could have something to do with the lack of signing. Every anti-malware product has its own rules for that.
Finally, there’s heuristics, which is the hardest of all for the dev to figure out. Only after first investigating the signature database possibility, and the rules possibility, should one deign to tackle the heuristics possibility. Every anti-malware’s heuristics algorithm is different; and many anti-malware products do it wrong. It is easy, in any case, for a dev, once he has figured-out that it’s a heuristics problem, to ask the anti-malware software maker to review the file(s) in question and determine if it’s a heuristic false positive; and then to add that to the whitelist portion of the database.
The sad-for-you fact is that I’ve FORGOTTEN more about how anti-malware works, in life, than you’ll likely ever know, there, Sparky.
It is, then, YOU who needs to get a clue…
…and to also maybe get some psychological help with your trolling and the backed-by-nothing-at-all, drive-by, one-liner, not-as-clever-as-you-think swipes it causes you to take at those who’s being smarter than you so vexes you.
__________________________________
Gregg L. DesElms
Napa, California USA
gregg at greggdeselms dot com
Veritas nihil veretur nisi abscondi.
Veritas nimium altercando amittitur.
Except that you aren’t an IT professional and never were. That is plain to see from someone who really has been doing this stuff for years.
Sorry tubby, not buying it.
Uh, huh. Hmm… so, then, let’s review: I’m here offering actual and substantive information that is either independently and provably verifiable and true, or not, including my real name in real life, through which my pushing 40 years in IT is MORE than easily verifiable.
You, on the other hand, are here under an alias; offering trollish one-liners, with absolutely NOTHING of substance to call into question or counter a single thing I’ve here (or anywhere else, for that matter; and they are many) written.
You are, in addition, clearly so flummoxed by it all that the best you and your immature sensibilities can come-up with is “tubby.” Ooooh. Ouch.
You wrote, “…from someone who really has been doing this stuff for years.”
My response: To a child, “years” is last Tuesday. And you are clearly a child… in more ways than one. Moreover, it would be very interesting to know how you define, in this context, “stuff.” Entry-level installation techs are a dime a dozen. They’re only one notch below the pimply-faced nerds to work in the service department at Best Buy and respond to every problem with re-installing Windows.
I’m really sorry — no, really… I am — that in your obviously low-level-functionary career as a mere board-swapper or equivalent, working however many levels below the IT Director or CIO (the kinds of positions I’ve held) that you were, said IT Director or CIO was unhappy with your couldn’t-be-anything-other-than substandard work and fired you; thereby causing you to now come into places like this and take immature and bereft-of-substance pot-shots at the very kind and level of IT professionals you so clearly despise. Please add that to your list of things you need to cover with your psychotherapist.
The bottom line, here, is that even the only slightly discerning reader (and so that wouldn’t include you, just in case you were unclear about it) is able to plainly see who’s credible, and who’s not.
troll | trōl/
noun: troll; plural noun: trolls
informal: a person who submits deliberately provcative online postings in forums, chat rooms, UseNet, and in comments beneath articles which are intended to incite angry responses, just for their own sake.
verb: troll; 3rd person present: trolls; past tense: trolled; past participle: trolled; gerund or present participle: trolling
informal: the act of submitting deliberately provcative online postings in forums, chat rooms, UseNet, and in comments beneath articles which are intended to incite angry responses, just for their own sake.
Please, “joe_ron,” stop being a troll. And get some help.
Hmm. Interesting. Who ever woulda’ thought that the whole youthful “too long didn’t read” (TLDR), and belief in that the world can be covered in 140 characters or less thing, about which I so often complain, could ever work in my favor. In this case, it has clearly left poor “joe_ron,” here, so completely ill-equipped to write anything actually substantive that this has been rather like shootin’ fish in a barrel.
[sigh] Oy. [shakes head in disbelief]
__________________________________
Gregg L. DesElms
Napa, California USA
gregg at greggdeselms dot com
Veritas nihil veretur nisi abscondi.
Veritas nimium altercando amittitur.
I am sorry that you spent time writing all of that, because I didn’t read it.
JOE_RON WROTE: I am sorry that you spent time writing all of that, because I didn’t read it.
MY RESPONSE: Uh, huh. Sure you didn’t. Don’t pee on my leg and then tell me it’s raining. You just can’t counter it, because you, me and God all know that you’re just a troll. Simple as that. No surprises.
Plus, don’t worry about me. I type better than 90 words per minute, with few errors; and I can lay it down pretty much the way I want it the first time, with few edits. What would take the likes of you two hours, I can do in seven to ten minutes. I’m more than happy to spend that amount of time shutting-down a troll like you. Consider it a public service.
__________________________________
Gregg L. DesElms
Napa, California USA
gregg at greggdeselms dot com
Veritas nihil veretur nisi abscondi.
Veritas nimium altercando amittitur.
Gregg, that was informative but more importantly hilarious 🙂 🙂 Sorry for bringing an old post to life.
If only he could get his point across with more brevity, fewer people would scroll past his comments.
The ZIP link on Git hub is not working
It Works Now.
Thank You 🙂