NetworkMiner – Capture Files On Network Traffic And Sniff Data Packets
Many network packet sniffing applications send requests and, in result, receive responses in order to calculate the packets passing through the network traffic. This not only increases the probability of getting incorrect results for number of packets that got through one specific session but also affects the decisions you make considering the packet sniffing analysis report. Apart from sniffing data packets, network admins sometimes need to fetch the data which is being accessed by different nodes on the network, this may includes, images, audio/video streams, messages etc. If you need an advanced network sniffing tool, which, along with observing data packets, can capture files and provide other important information regarding requested server hosts, DNS table, connected clients, passive and active sessions and so on, NetworkMiner bundles the right set of tools you’ve been looking for.
It’s a feature-rich host-centric network forensic analysis tool which is meant to sniff data packets, connected clients data, and other host of information which a network admin require each time before creating network performance and usage related reports. While you’re online, it uses PCAP information files for saving results, which can also be parsed for offline viewing in order to do further analysis. Unlike conventional data sniffing tools, its major focus is on collected network hosts related information instead of collecting traffic data on the network.
While it offers multi-tab unified UI to easily switch between different informational windows; you can, at any time, start and stop the capturing process or analyze current network status by stopping the real-time analysis. Before you start analysis, choose your network adapter from the pull-down menu and hit Start present next to it.
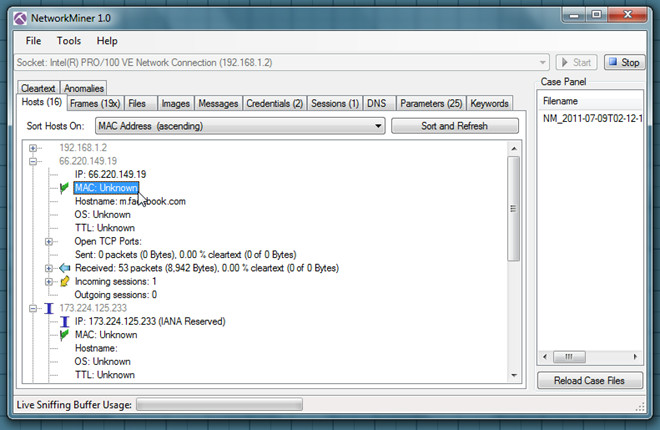
Under Hosts windows, it shows connected hosts with info, like MAC address, IPv4 address, TTL, Open TCP ports, data sent and received details, incoming and outgoing sessions. You can also choose to sort listed hosts according to MAC address, Host address, Router hops distance, Number of open TCP ports, Operating System, etc.
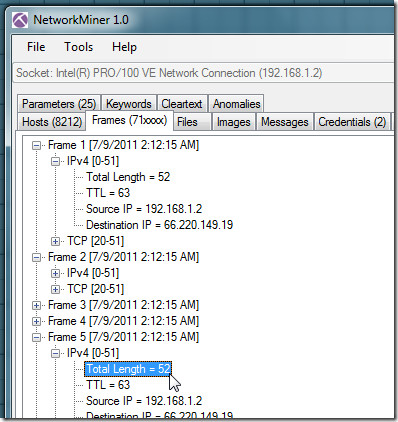
The Frames window deals with captured network frames. It allows you to see IPv4/v6 information, like, total length, TTL, source and destination IP. Similarly, TCP header includes source port number, destination port, sequence number and FLAGS.
Likewise, you can see captured files, images and messages from respective tabs. NeworkMiner has the ability to capture cookies containing approved/unapproved credentials, which can be seen from Credentials tab.
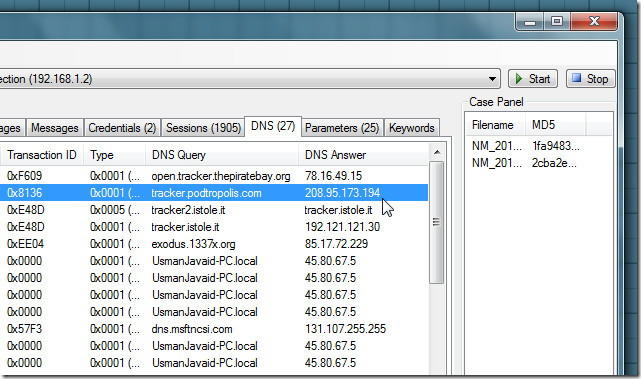
The Session window lets you view all the client hosts on the network with their sessions information. You will be able to check destination server host address, S.port and start time of the session. From DNS window, you can check all the DNS server queries and their responses along with details regarding Client address and port, server address and port, Transaction ID, etc.
The right sidebar holds current case files which contain all the previously collected information, current details and files which are being captured. You can access these files anytime from Captures folder residing in NetworkMiner folder. When you want to analyze the captured details offline, you will have to open the previously saved PCAP file from File menu. NetworkMiner is an open source application that supports both client and server editions of Windows OS platforms.
