DeEgger Embedder: Hide Private Files Within Images, Videos Or Audio (Media Steganography)
If you are oblivious of the term Steganography, you might be missing on one of the most widely used methods of securing important data. It is a technique that allows you to embed one file into another. The purpose of which, is to hide the original file, make it devious to an unintended recipient by concealing it within a fake one. If a certain sensitive information you consider is yours prerogative only, then using a steganography application is advisable to keep it away from others. There are various Windows application at your disposal (both paid and free) that does this job and back in 2010, Aatif reviewed SilentEye, which uses the steganography technique to hide confidential data. We have another similar application for you labeled as Deegger Embedder, which offers the same facility, but with support for additional media formats. This free steganography software is designed to merge two or more files together, supports a wide range of file extensions you can hide and lets you create the bogus file in AVI, JPEG, MP3, MP4, PDF, PNG and other formats.
The entire process of combining and extracting a file is quite simple. All you need is to select your host file and embed file via simple drag & drop. You may however, also use the browse button on the right side of the window to select your files. As stated earlier, you can embed as many files into a single file as you want. Once, you have added your source and embed files, simply click Combine button at the bottom to save your bogus file, making the woven file within completely hidden to any third person.
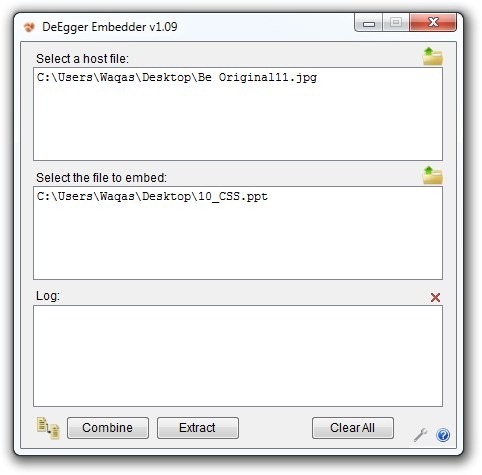
Did I mention you can use the same tool to decrypt your file? All you have to do is click the Extract button to choose the steganographic file that you just created and click Open, in the following window. It will then ask you to select the target folder for file extraction, simply choose your output directory and click Save to extract your original file.
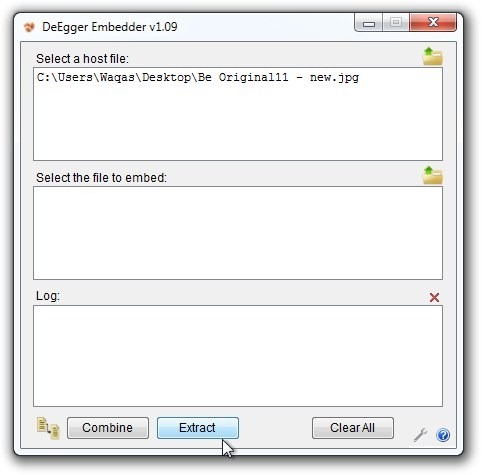
You may click the Settings button at the bottom right of the window to open up a configuration console, where you can switch between singe, multi-host and parallel modes, enable/disable read-only and modify timestamp embedding options, and change view settings.
The utility works on both 32-bit and 64-bit OS editions of Windows and supports Windows XP, Windows Vista, Windows 7 and Windows 8.

Products like this are pretty cool, methinks. Plus, after someone beats me over the head until I decrypt my file, why would they raise question when the only files in it are some receipts and a picture of grandma? Why would they think I’ve embedded a top secret file in the pic?
Something like this is not meant for encrypting files on your own computer, it is meant for passing information to a second party without a third party knowing (and if they do, they can not decrypt it unless they have the original image). It can be one of the most secure methods of encrypting data. The original image acts as both the envelope to embed the message in (one that can be displayed on public websites, or sent out masquerading as junk email — spam), as well as acting as the first “password” of sorts (unless you have the original image, it’s is extremely to impossibly hard to extract the embedded message). As Andre commented, though, it is always good to password/encrypt the message that will be embedded.
Again, this is not something you use to hide files on your computer (although it can be used for that if that excites you for some reason). What this is really for is as something one uses to pass messages to others located remotely, who you may not even know personally (such as if their identities have been hidden from you). i.e. you grab a digital camera, take several photos, download copies to your computer and hand the camera to your partner in crime. The partner then physically passes copies of the images to anyone else who needs them while you are somewhere else, encoding messages in those messages and posting them on your “”cooking blog.”” The only people who know that there are messages in these publicly accessible images are the ones who have been told, and only those who have original images can extract your messages from them.
If you are leading a revolution against the government in Iran, or spying for the Russians, or something on this kind of level, something like this WILL be very useful and rather secure.
If you do not engage in these types of activities, this program would NOT be of much use to you, except maybe as a gimmick you show your buddies as you drink Mt Dew and play WOW.
Products like this are gimmicks: if you’re serious about securing your files, why not just use something like TrueCrypt?
This is not very secure if it doesn’t allow you to password protect the extraction process. better off just zipping the file with a password.