How to Use Tor: A Guide to Getting Started
Online privacy is something everyone thinks about these days. Casual internet users are concerned about where their data is going, who has access to it, and what harm it could cause if the wrong people get their hands on it. Even the companies that provide internet service are allowed to use or even sell private data, putting everyone at risk.
Fortunately, there are tools like the Tor network that help preserve some of those basic freedoms.
A little anonymity can go a long way.
What is Tor?
When you connect to the internet you’re assigned an IP address by your service provider. This IP is easily traceable to your name and physical location, and it’s directly tied with your unencrypted web browsing activity, as well. ISPs can monitor, log, and even sell this data to third parties without your consent. That’s where Tor comes into play.
Tor is a network built around anonymity. It’s managed by The Tor Project and has been operational since 2002, though precursors to Tor can be traced back even further. Tor works by using onion routing to encapsulate data in layers of encryption and passing that data through a series of nodes. Each node peels away one layer of encryption, revealing the next layer along with instructions on where the data goes next. By the time the final layer is decrypted, the data will reach its location, leaving almost no trace behind.
Using the Tor network is a bit like passing a note across a crowded room of people, each of whom has their eyes closed. You pass it to someone at random, that person passes it to another person, and so on. When it reaches the other side of the room, nobody knows who the note originated from, nor can they tell which person handed it to them. The Tor network protects your identity by encrypting your traffic and making everything you do as anonymous as possible.
Tor and the Tor Browser
The Tor network is used by a number of different software suites, the most well-known of which is the Tor Browser. The Tor Browser works like any other browser, only instead of sending information directly to and from your computer, it leverages the Tor network to provide a strong measure of privacy and anonymity.
The Tor Browser is basically a highly customized version of Firefox. This gives it the ability to access any part of the web, just like a regular browser. However, due to its security conscious design, the Tor Browser disables a number of common web technologies such as Adobe Flash and JavaScript, rendering many websites unusable.
The Tor Browser is an open source project with versions available for Windows, Mac, and Linux computers as well as smartphone and tablet releases for devices running Android. Third parties have created unofficial versions of the browser that also use the Tor network, giving iPhone and iPad owners the ability to sure safely, as well.
Installing the Tor Browser
Using the Tor Browser is the most direct way of leveraging the privacy power of the Tor network. It’s simple, it’s direct, it’s free, and it’s easy to get started. There are several ways to download and install the browser, including portable versions, unstable versions, and compiling directly from the source. Most people who use the Tor Browser get it through the Tor Browser Bundle. This is by far the easiest way to access the Tor network, as everything you need is packaged into a single download you can run and install with just a few clicks.
Install on Windows
- Visit the Tor Browser Bundle download page in your web browser.
- Click the purple “Download” button. You may need to change operating system options to get the right version.
- When the file downloads, run the installer.
- Launch the Tor browser when the installation completes.
- Click “Connect” to access the Tor network.
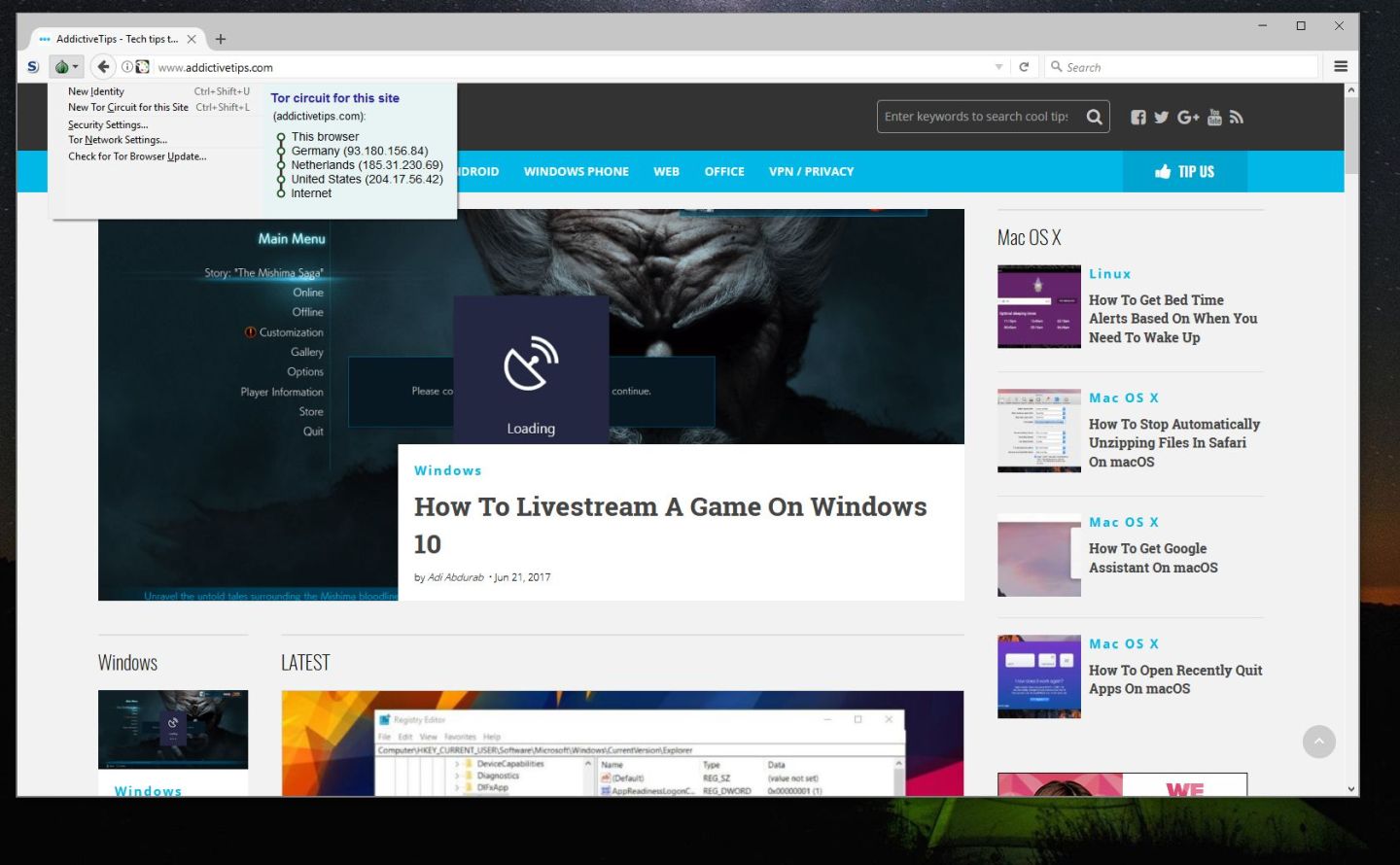
- Click the onion icon just to the left of the URL bar.
- Choose “Security settings”
- Move the slider all the way up to “High” for maximum privacy.
- Surf the web through the Tor Browser.
Install on MacOS
- Visit the Tor Browser Bundle download page in your web browser.
- Click the purple “Download” button. You may need to change operating system options to get the right version.
- Save the file on your computer.
- Click to open the .dmg file.
- Drag the included file into your Applications folder.
- Pin the Tor Browser on your dock and launch it.
- Click “Connect” to access the Tor network.
- Click the onion icon just to the left of the URL bar.
- Choose “Security settings”
- Move the slider all the way up to “High” for maximum privacy.
- Surf the web through the Tor Browser.
Install on Linux
- Visit the Tor Browser Bundle download page in your web browser.
- Click the purple “Download” button. You may need to change operating system options to get the right version.
- Save the file to a local directory.
- Open a terminal and type the following command: tar -xvJf tor-browser-linux32-6.5.2_LANG.tar.xz
- In the line above, replace the 32 with a 64 if you downloaded the 64-bit version, and switch LANG with the language you downloaded. You might need to adjust the version numbers if the file notes something different, as well.
- Switch to the Tor Browser directory in the terminal, replacing LANG with your language code: cd tor-browser_LANG
- Run the Tor Browser.
- The Tor Launcher will appear on your screen. Connect through this and the browser will open.
- Surf the web through the Tor Browser.
Install on Android
There’s an official Tor Browser for Android called Orfox. To let it use the Tor network, however, you’ll need to install another program first. Both are open source and available through Google Play.
- First, install Orbot from Google Play.
- Run Orbot and let it stay active in the background.
- Install Orfox, the Tor Browser for Android, from Google Play.
- Launch Orfox and use it to surf the web with enhanced Tor network security.
Install on iOS
The Tor Project doesn’t maintain an official Tor Browser for iPhone, iPad, or other iOS devices. There is a free and open source Onion Browser created by Mike Tigas that leverages the Tor network performs most of the same functions.
- Visit the Onion Browser download page on the iTunes App Store.
- Install the app on your iPhone or iPad.
- Surf the web through the Onion Browser.
Change Your Habits for Better Privacy

It’s a common misconception that installing and using the Tor Browser is a bulletproof solution for all online dangers. Using the Tor network does have a wide range of advantages, but it’s far from a quick data privacy cure-all. You’ll need to change some of your normal web browsing habits to ensure you remain anonymous. This involves disabling certain plug-ins, keeping an eye on cloud storage programs, and being smart about which websites you log into.
Follow these tips to ensure a higher level of privacy online:
Use HTTPS versions of websites – You’re probably familiar with the “http” letters used at the beginning of websites. That extra “s” denotes secured versions of those sites and means they encrypt the data that goes to and from their servers. Most shopping, e-mail, and banking services use HTTPS by default. The data passed to and from a Tor exit node to the intended website is unencrypted, making it an extremely weak part of the process. If you connect to a secure HTTPS site, you’re a lot safer. The Tor Browser Bundle includes the HTTPS Everywhere extension, which forces secure connections with major websites whenever possible.
Don’t use plug-ins or add-ons – The Tor Browser is based on Firefox, which means it’s possible to use a handful of Firefox add-ons just like an ordinary browser. The Tor Browser Bundle even comes with a few security-minded add-ons pre-installed, such as HTTPS Everywhere and NoScript, all of which are safe to use and enhance your anonymity. To stay as secure as possible, you should leave the plug-ins list at that. Adding new plug-ins could put your privacy at risk, both by directly circumventing Tor protection and by encouraging you to relax your habits while using the Tor Browser.
Disable JavaScript, Flash, ActiveX, Java, and QuickTime – Technologies like these power a great deal of the web’s interactive content. They can also compromise your privacy by sharing information about your system and location with websites, even if you’re using the Tor network. The Tor Browser disables all of these on its high and medium security settings.
Don’t use torrents over Tor – Many file sharing and torrent applications are known to ignore proxy settings and connect directly to trackers even when instructed otherwise. If you configure your torrent software to use the Tor network, it simply might not do it. [In case you want to use it, we have found the best VPNs for torrenting, the ones that actually take your privacy serious]
Don’t log into anything through Tor – One of the first things people do when getting on the internet is to log in and check their e-mail. While this is certainly possible through the Tor Browser, it kind of defeats the purpose of the entire network, as you’re still sharing data with outside sources. For the ultimate in privacy, don’t log into any website or provide details of any account while using Tor.
Don’t open files downloaded through Tor – This is a commonly ignored piece of advice that can completely destroy your online privacy. Most users browsing through Tor are interested in accessing sensitive information. If they download a file through the Tor Browser and open it, that file could access the internet without passing through the Tor network, thus sharing your real IP and location. It’s best to disconnect from the internet before opening any downloaded content.
Use Tails OS – The Tails OS was designed to use the Tor network. Everything that passes through the operating system is encrypted and anonymized, and there’s no trace of data left behind. Tails even runs from a DVD, SD card, or USB stick with no installation required. With Tails and the Tor Browser both in use, your online activities are much more secure. See the section below for more information on how to install and use Tails OS.
Using Tor with the Tails Operating System
Tails is a lightweight live operating system designed to keep private data private safe and leave no trace of information on the device it’s running on. It uses state-of-the-art cryptographic tools to protect your data and allow you to circumvent censorship almost anywhere you go. Better still, Tails runs on almost any computer simply by inserting a DVD, USB stick, or SD card.
Tails uses the Tor network by default, encrypting and anonymizing every piece of information that leaves your computer. It also comes with the Tor Browser and a secure instant messaging service to make all of your online activities as private and anonymous as possible.
To use the Tails operating system you’ll need two USB sticks and a separate internet device to read instructions while the installation takes place. The website below walks you through the process step by step.
- Use your web browser to download Tails OS.
- Run the Tails installer and follow the on screen instructions.
- Restart your computer and boot directly into Tails OS.
- Enter your Wi-Fi or connection details to access the internet.
- Open Tor (included with the Tails download) and browse the web at your leisure.
Tor and the Dark Web
Tor and the dark web have a long history together. Using the Tor network is the only way you can access .onion links, which is where most of the deep web’s content is hidden. The Tor Browser also provides a bit of security for anyone exploring the hidden depths of the dark web. The two are closely linked, but it’s important to realize that all Tor users aren’t necessarily using the browser or the network to access illicit content. Privacy is still Tor’s number one focus.
If you intend on using the Tor Browser to access the dark web, you’ll need to take every precaution to preserve your privacy. Read our full guide on How to Access the Dark Web and Deep Web for more information.
Can You Use Tor for Everyday Browsing?
While it’s possible to use Tor or the Tor browser for everyday tasks on the internet, most users find it’s an exercise in frustration. With all of the encryption and re-routing that’s going on, Tor tends to be extremely slow, sometimes as much as 70% slower than your home internet. This leads to endless waits for pages to load and drops download speeds to practically nothing. On top of that, because Tor disables so many modern web technologies that are inherently unsafe, you’ll find many common websites such as YouTube are completely inaccessible.
The Tor Browser is a great tool for accessing certain websites, especially geo-restricted content, censored websites, and content sealed up on the dark web through onion links. When you’re traveling it’s not a bad idea to use Tor for basic tasks, either, and it does wonders for anyone who lives in an area where certain websites are blocked or restricted. It’s also great for journalists who need to preserve their anonymity while researching and passing information to other sources. You’ll need a lot of patience if you use it for all of your daily internet tasks, however.
Isn’t Using a Regular Browser’s Incognito Mode Safe Enough?
Private tabs on browsers like Chrome, Firefox, Opera, and Safari were made for one purpose: hiding online activity from your local computer. In essence, all they do is make sure everything you access in a private tab doesn’t leave a trail in your local browsing history. Incognito mode doesn’t prevent ISPs from tracking you, nor will it protect your privacy once data leaves your computer.
Tor versus Proxies
Using a proxy to hide your location sounds like a similar solution as using the Tor network. They both help bypass censorship laws, they both make users anonymous, and both protect a user’s location and online activities. The difference lies in how each of these services provide anonymity.
With a proxy your traffic is directed through a non-local server, assigning you a different IP address so activity can’t be linked to your computer. The downside of using a proxy is that it creates a single point of failure. The proxy provider knows who you are, especially if you pay to use the service. This means they can unlock your encrypted data and use it for their own purposes, all without your knowledge. Using a proxy can be dangerous if privacy is important to you, especially if it’s a low quality or free proxy.
Tor neatly circumvents the limitations of a proxy by distributing its anonymizing services over thousands of computers. Instead of sending your traffic through one non-local server, it’s sent through at least three, completely at random, and all encrypted. It’s difficult, if not impossible, to track the path data travels through the Tor network.
Using Tor with a VPN
Using Tor alone isn’t enough to protect your online browsing habits. Even with the encryption and anonymity provided by the network, it’s still possible to monitor someone’s traffic, analyze it, and find its source. While measures such as these are usually reserved for high value targets, there are still a number of reasons you should pair Tor with a virtual private network.
Somewhat similar to Tor, VPNs encrypt your internet traffic and allow it to pass through your local ISP anonymously. Information is sent to a server of your choosing, then it gets decrypted and utilized back on your own device. The privacy offered by a VPN is more focused on preventing data leaks, not obscuring your identity, but there’s some overlap between the two.
IPVanish is a highly reputable VPN service. For our readers they have some extremely competitive deals. Their plans range from one month up to a year, with an impressive 60% discount for the full 12 month subscription — that’s only $4.87 per month. And they also throw in a no-questions-asked 7 day money back guarantee in case you need to test drive their service.
There are two ways to use Tor with a VPN. Both carry some drawbacks and benefits, but both also provide extra privacy over using one or the other.
Method 1: VPN to the Tor Network – The simplest way to use a VPN with Tor is to sign up for a VPN service, download the Tor Browser, then have both of them running at the same time. This method sends data through your VPN first, then through the Tor network for an extra measure of anonymity. It’s also extremely easy to do. The downside is that the typical Tor exit node vulnerability still applies, meaning your data could theoretically be tracked if someone was determined enough to do so.
Method 2: Tor Network to a VPN – This is the commonly suggested method of combining Tor with a VPN. Data goes from your computer, through the Tor network where it’s encrypted and anonymized, then through your VPN. This reduces the risks of a VPN logging your information, as data the VPN receives will already be anonymized through the Tor network. The set-up is a bit more convoluted, however, as you’ll need to use a security-oriented operating system such as Whonix to make sure data follows the correct path.
If you need a VPN for a short while when traveling for example, you can get our top ranked VPN free of charge. NordVPN includes a 30-day money-back guarantee. You will need to pay for the subscription, that’s a fact, but it allows full access for 30 days and then you cancel for a full refund. Their no-questions-asked cancellation policy lives up to its name.

The dark web is a thing that everyone has to see. But guys, please use a VPN when you are going there because it is unsafe. I use NordVPN in this case because it is the safest VPN on the market.
The bogus notion of the “Internet Service Provider” should end!… and everyone should become their own ISP!
.
Who, and what, gives ISPs the RIGHT to “provide” A-N-Y-T-H-I-N-G, T-O A-N-Y-O-N-E?… and why must netizens go through “their gateway” in order to access the Internet? In addition!… in the light of the FACT that most “ISPs” use Closed Source Software AND hardware, “ISPs” are in a systemic breach of the RIGHT of netizens, to choose the FOSS and FOSH ICT medium that/ which is in accordance with their individual and collective Digital Human Rights! But!… and more importantly!… netizens have a right to the ASSURANCE that the ICT invoked by an “ISP”, isn’t working– in the booth, in the back, in the corner, in the dark!– in COLLUSION with sundry interests, and in violation of their individual and collective Digital Human Rights!
.
To sum up… an International Conference should be established, that/ which explores the efficiency, effectiveness, and ethos, of the “ISP”! For simply!… the day of the pedantic, paternalistic, pretentious, and prickish ISP pap, is in need of a swift end!
.
Please!… no emails!
FYI, ExpressVPN hosts their own Tor servers. I don’t know of any other VPN service that does it.