How to Use Tor With a VPN: Tutorial to Install IPVanish
If you’re less than 100% familiar with how to use Tor with a VPN, you’re in good company. Both technologies offer sophisticated methods to lock down your privacy online, but using them in tandem is surprisingly easy. Today, we’ll lay out how to get started using VPNs and Tor together, step by step.
Tor is an anonymity network that spans the globe and works to ensure that its users are protected from censorship, detection and invasion of privacy. Its current name is derived from “The Onion Router”, which was its original project name. Onion routing itself is what the Tor network uses, by encrypting and redirecting information throughout its network multiple times before it reaches its destination. This adds “layers” of encryption, hence the “onion” in onion routing.
The history of Tor is fascinating: What would become Tor was originally developed by the US Navy and DARPA. DARPA’s contributions are of particular note, since their ARPANET is the ancestor of our modern-day internet. The goal of Tor back then was essentially the same as it is now: to allow for private, encrypted communications to take place between its users.
Since its inception, Tor has evolved to become a tool used by many types of people all over the world. This tool can be used to leak and blow the whistle on unscrupulous government or corporate doings, to safely communicate with journalists without fear of being tracked, to browse less secure parts of the internet’s underbelly, and so much more. Using Tor can be legal or illegal, but in either case its users enjoy great anonymity and privacy from third-party or government snooping.
Today, we’re going to discuss two of the biggest names in privacy: Tor and VPNs. More specifically, we’re going to dive into how these technologies can be used together and why it’s worth the effort. Additionally, we’ll cover how to use IPVanish with Tor, which is one of our most highly recommended VPN services for Tor. We’ll start with the basics first.
What is a VPN?
A VPN is a Virtual Private Network. This technology has existed for some time, and chances are you may have already encountered it without knowing it. Many school and business networks use VPNs to increase security and allow secure remote access to the network for their employees and faculty. This implementation of VPN technology isn’t generally focused on anonymity or a high level of encryption, but this can vary on a case-to-case basis.
A more common and prominent implementation of VPN technology is known as Commercial VPN. Commercial VPNs, as the name implies, are VPNs that allow paying consumers to access their networks. These VPNs have a strong focus on privacy, often encrypting data to such a point that neither an ISP or government can decrypt it. Many of them come with an assortment of extra features, but the primary goals of a VPN provider are to provide privacy and security to their users, with the occasional side of geo-spoofing and specialized encrypted messaging apps.
While Tor works through “layers” of encryption and redirections, VPNs use various VPN protocols to protect and anonymize their data. These protocols, like L2TP and OpenVPN, offer great performance and much lower latency than the Tor network, allowing users to more easily share files and stream video than your typical Tor connection would allow.
Both of these technologies are prominent. Both serve similar purposes. So you may be asking yourself the following question:
Why use Tor with a VPN?
It’s easy to see what Tor and VPNs have in common: They’re both made to protect the privacy of the user and the security of their data. They’re both capable of bypassing government censorship and allowing for safe, encrypted communication between their users. There are a few key differentiators, however, and we’ll go over those now.
VPNs are:
- Much faster, thank to VPN protocols designed to maximize speed while still using secure encryption.
- Generally, a premium option, as free VPNs either offer a poor experience or are simply unsafe to use.
- Far better suited to filesharing.
Tor is:
- Much slower than a VPN, due to the nature of onion routing and its encryption. In theory, this could make Tor more secure, but the latest VPN protocols have yet to be broken.
- A completely free, open source application via the Tor Browser. You don’t have to pay a cent for Tor’s great security.
- Poorly suited to filesharing and related applications due to slow network speeds.
- Allows access to .onion domains. These domains are only accessible via Tor, and offer access to secure, hidden services.
Their security benefits differ, too. VPNs are designed to hide your traffic from your ISP through their encryption, while Tor is made to hide you while you’re using the Tor network. ISPs can detect both types of traffic, even if they can’t access it.
Most security compromises of either networking solution are down to user error, but there are a few worth noting. VPNs are extremely secure, unless your provider keeps detailed logs of your activity, which could allow authorities to trace your usage of the VPN back to you. Tor, meanwhile, is designed in such a way that many nodes within its onion routing would need to be compromised (or the PCs of its users would need to be compromised despite Tor’s security settings) in order to pose a threat to its users.
The first is quite possible, and relies entirely on your VPN provider. The second is much less likely, but if you’re an enemy of a government or are actively being harassed by one, for example, this is still a possibility that you’ll likely prefer to avoid.
So, why use Tor with a VPN? The simple answer is to remove all the risk of communicating through the internet. There’re two ways to go about this:
- Routing your Tor traffic through a VPN will make you virtually invisible. Even if someone manages to compromise you on Tor’s end, all they’ll get is a false IP from your VPN that won’t lead them anywhere. (Just be sure your provider isn’t keeping logs!)
- Routing your VPN traffic through Tor effectively means that even your VPN provider has no idea who or where you are, even if they are keeping logs. This is an effective measure for folks who don’t trust their providers not to keep logs.
How can I use Tor with a VPN?
Method 1 is pretty simple. All you need to do is enable your VPN service and start using Tor. This method is VPN-to-Tor, which will protect you from any compromises on Tor’s end but won’t protect you from user error or VPN logging.
Method 2 is a bit harder to set up, and not all providers will support it. Tor-to-VPN requires either a supported provider, or usage of specialized network hardware like PORTAL or a virtual machine like Whonix.
Below, we’ll teach you method 1 with IPVanish. Since it’s a relatively easy setup, you shouldn’t have many problems–most VPN providers should work similarly.
Read our full IPVanish review.
Method 1: VPN-To-Tor (Recommended with IPVanish and Other Log-less Providers)
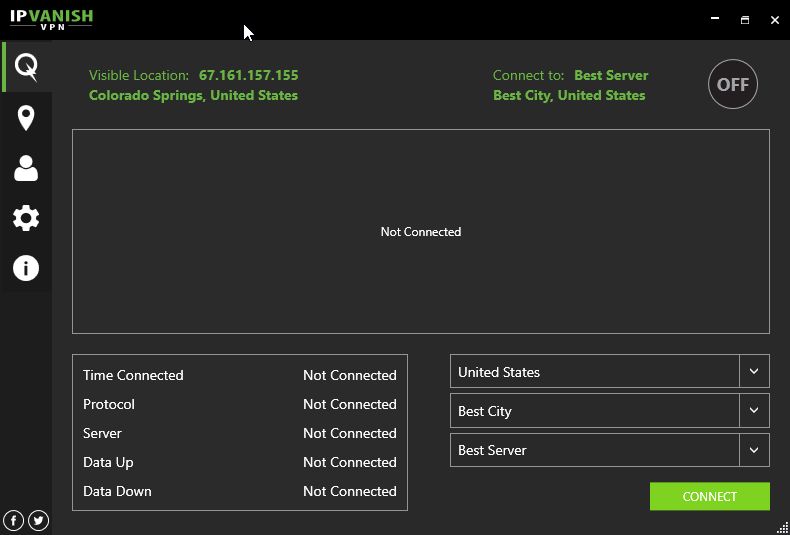
First, open up IPVanish. Your screen should look something like this:
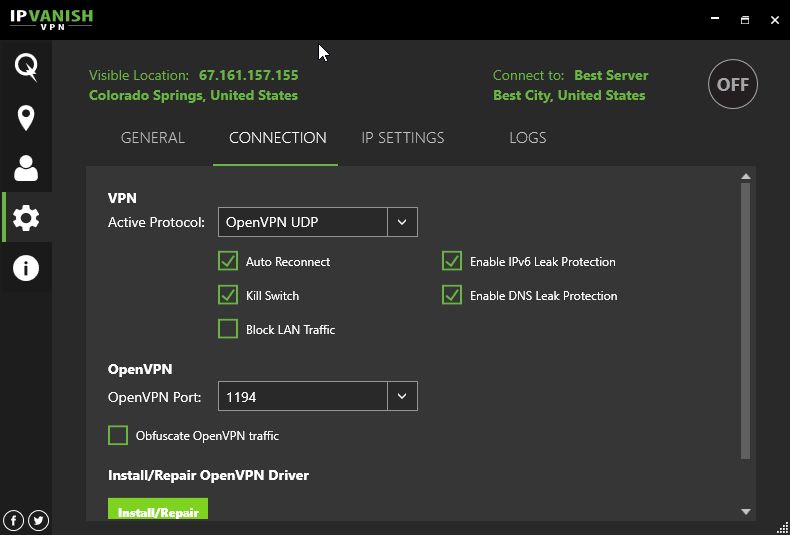
Before connecting on the bottom right, click the Gear icon on the left and then the Connection tab.
After verifying that your settings match ours, return to your main screen and then click “Connect.” (Note that enabling Kill Switch will disable all non-VPN internet traffic on your device, enhancing your security.)
Now, open your browser of choice and open IPVanish’s tool to verify that your VPN connection is working properly. If it is, you can now access Tor.
First, go ahead and download the Tor Browser Bundle if you don’t already have it. Once you’ve downloaded it, place it somewhere on your PC where it’s easy to access (I prefer Desktop or Documents), then open the Tor Browser folder.
Click the “Start Tor Browser” shortcut to open Tor.
Congratulations! You’re now using Tor through a VPN. Be sure to do all of your most important browsing on the Tor Browser – save content streaming or downloads for your raw VPN connection (if possible) to maximize your performance.
IPVanish offers a 7-day money back guarantee which means you have a week to test it risk-free. Please note that Addictive Tips readers can save a massive 60% here on the IPVanish annual plan, taking the monthly price down to only $4.87/mo.
Using other VPN providers with Tor
Method 1: VPN-to-Tor
Any VPN-to-Tor implementation should work in pretty much the same way as the IPVanish tutorial. Just be sure that you have Kill Switch enabled and you aren’t prone to DNS/IPv6 leaks. Once you have those settings enabled, simply connect to your VPN provider of choice, verify they’re working properly and connect to Tor.
Method 2: Tor-to-VPN
A PORTAL router requires one of the supported routers listed on this page and OpenWRT. Verify that your hardware is compatible before going through their setup tutorial. Once you’ve verified that this is the case, this is a one-and-done solution that you don’t need to think about after you’ve already enabled it.
Whonix can be used on your pre-existing computer, but will also require you download and install VirtualBox. Follow tutorials for both, and within your Whonix VM, install and run your VPN software the same way you would normally on your desktop.
Conclusion
And that’s it! We hope this tutorial helped you learn how to implement your Tor and VPN connections, or at least answered any questions you may have had about the two networking implementations and why they might be used together. Feel free to sound off in the comments below if you need any assistance!
If you need a VPN for a short while when traveling for example, you can get our top ranked VPN free of charge. NordVPN includes a 30-day money-back guarantee. You will need to pay for the subscription, that’s a fact, but it allows full access for 30 days and then you cancel for a full refund. Their no-questions-asked cancellation policy lives up to its name.

I am a little confused about my vpn. I use Biteefender total security suite on my cpu. My concern is I have TOR on a removable Zip drive.would you just use the vpn on the computer or download a Possibly better vpn and try to put it on the Zip drive that has my TOR on it?
When using Tor over VPN (Start VPN, then Tor), choose wisely who your VPN is. If by some miracle that your adversaries managed to crack Tor and see that you’re using a VPN, the VPN could easily rat you out, especially if that VPN is based in a 14 eyes country.