What Happens if VPNs Get Blocked? SSH Tunneling Explained
With net neutrality under attack, it’s important to learn how to guarantee your own freedoms. Today, we’ll show you how to set up SSH tunneling on your device, which along with a VPN, and be used to unblock Internet connections in even the most repressive countries.
The issue of net neutrality has slowly become a worldwide concern. With big companies and ISPs fighting to control the internet, more and more people are turning to alternative methods to keep the web open and free. For every measure there’s a counter measure, however, which means this fight could go on for a very long time.
VPN block got you down? Switch to one of the providers to restore access to the open Internet:
-
- NordVPN – Best SSH Alternative – NordVPN is the MacGuyver of the cybersecurity world, capable of getting you past the harshest Internet restrictions. Always a step ahead of VPN bans the world over.
- Surfshark – A modernized VPN with all the latest encryption protocols and a RAM-only network for anonymity. Beats most VPN blocks.
- ExpressVPN – Tried and true champion of digital rights the world over. Outstanding connection speeds.
One of the most popular tools used to preserve online anonymity is virtual private networks. VPNs encrypt data before they leave your device, keeping it safe from prying eyes and routing it through an external network of servers to add a measure of anonymity. VPNs can help fight back against repealed net neutrality laws and internet fast lanes, but they’re not perfect solutions. In fact, ISPs can completely nullify VPNs by blacklisting the shared IP addresses most providers offer to their users. Nevertheless, there are still ways to access the free and open internet, including SSH tunneling and even some other features offered by a select few VPN providers.
VPNs and Net Neutrality
Virtual private networks restore a lot of online freedoms to regular internet users. They add encryption and anonymity, they break through censorship barriers, and they even make geo-blocking easy to bypass. In areas where net neutrality has bee repealed, VPNs also help restore unbiased access to the web. Sometimes they can even defeat tiered packages or even internet fast lanes!
The downside to VPNs is that ISPs can block them without too much trouble. In this case, you’ll need to look for alternative encryption methods to break through anti-neutrality barriers. There are plenty of protocols out there that can help you do this, but SSH tunneling is one of the most popular.
The Basics of SSH Tunneling
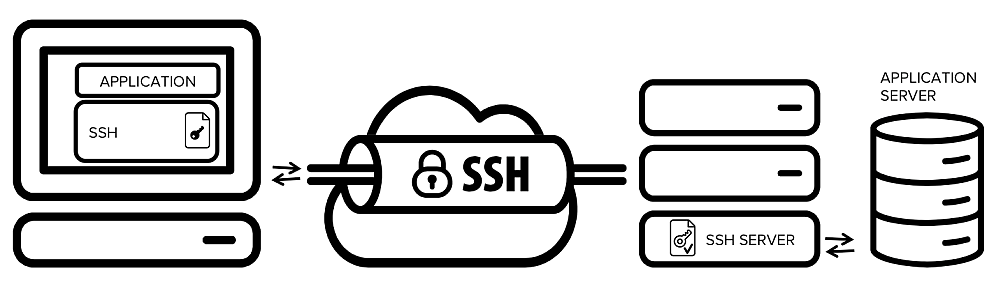
SSH tunneling, or secure shell tunneling, is more common than you might think. The protocol was developed in 1995 and has been in constant use ever since, starting with SSH1, evolving to SSH2, and eventually turning into OpenSSH. SSH is used to transfer unencrypted traffic over a network through an encrypted channel, essentially building a tunnel that can carry any type of packet. SSH is mostly used for small file transfers and remote server uploads, though it does have a number of uses beyond the terminal window.
Benefits of SSH Tunnels
The simplicity of SSH encryption makes it a surprisingly useful protocol, especially since it wasn’t designed for breaking through firewalls, merely transferring files securely. If you live in a place like China, Russia, or Turkey, however, SSH tunneling can help you access blocked content, since SSH itself is largely unmonitored. You can also use these tunnels to defeat ISP throttling since they travel through unique ports.
One of the most widespread modern uses of SSH is to securely access websites that block VPNs. If your virtual private network service is locked out, simply switch to the SSH tunneling option, hit the reload button, and the content will show up right away.
Drawbacks to SSH Tunneling
Even though it has been consistently maintained for decades, SSH is an old school-style protocol built when the internet was much smaller than it is today. Downloading gigabyte movies or streaming HD video content just wasn’t part of the web back then. For this reason, most modern users will view SSH as an incredibly slow method of encryption, poorly suited for anything beyond viewing websites or sending e-mail.
Due to the nature of SSH tunnel traffic, you’ll need to use it with a VPN that natively supports the protocol. Most public VPN services don’t allow SSH, unfortunately, which means you’ll have to create your own self-hosted VPN or find a public product with good SSH support.
Another drawback to the SSH tunnel experience is the protocol can be blocked. SSH traffic is detectible, just like VPN traffic. It’s a little more difficult to sniff out, but certainly not impossible. Because SSH has a ton of legitimate uses, though, it’s rare to see it blocked by ISPs or government censors. Removing SSH entirely would destroy legitimate uses of the protocol, so it’s generally left alone.
How to Create an SSH Tunnel
Creating an SSH tunnel isn’t as difficult as you might think. It’s also not a one-click process, though, so you’ll need to spend some time familiarizing yourself with some basic pieces of software. You’ll need to have an active VPN you can connect to to route your tunnel traffic through. Follow our guide on creating your own self-hosted VPN to get started, then come back here to get the SSH tunnel up and running.
Easiest Method – Use a VPN with SSH Support
There are only a few major VPN services that offer native support for SSH. If your VPN already offers SSH tunnels, all you have to do to take advantage of them is find the option in your local software and switch it on. No PuTTY configurations or terminal work, just a quick and easy settings toggle.
SSH Tunnels on Windows
Setting up an SSH tunnel to use on Windows isn’t terribly complicated. Once you’ve got your custom VPN up and running, all you need to do is download PuTTY and configure it for SSH tunneling. Follow the steps below and you’ll be set!
- Download PuTTY and open the program.
- In the “Host Name” box, enter the address of your VPN.
- In the menu tree to the left, unfold “SSH” and click on “Tunnels”
- Enter 8080 as the port. Make sure both “Auto” and “Dynamic” are selected, then click “Add”
- Click “Session” on the left menu to back to the main screen.
- Type a name in the top box beneath “Saved Sessions”, then click “Save”
- Click “Open” to connect to the server.
- A PuTTY security alert window will open. Click “Yes”
- Enter your server username and password and press ENTER.
Each time you start your computer you’ll need to run PuTTY and initiate the SSH tunnel. Since we created a saved session you won’t have to enter all the information again, simply choose the option and it will connect automatically.
SSH Tunnels on Mac and Linux
The more terminal-friendly Mac and Linux environments make SSH tunnels a breeze. No external downloads or installations are necessary, just make sure your VPN is running, open a terminal window, then enter the following command using your custom details.
ssh -ND 8080 user@your.server.com
Setting Your Browser to Use the SSH Tunnel
Setting up an SSH tunnel doesn’t automatically route your traffic through it. You need to set each web-accessible app to specifically use the tunnel’s encryption. Since we’re concerned with open internet access, we’ll be setting our browsers to use SSH by switching proxy details. Follow the guides below and you’ll be good to go.
Use SSH with Firefox:
- Create and run your SSH tunnel.
- In Firefox, go to the Settings menu and select Manual proxy configuration
- Next to “SOCKS Host” enter “localhost” without the quotes followed by 8080 as the port.
- Select SOCKS v5 below.
- Save the settings.
Use SSH with Chrome:
- Create and run your SSH tunnel.
- In Chrome, go to Preferences, then select “Under the Hood”
- Beside Network click “Change Proxy Settings”
- Select “Manual Proxy Configuration”
- Next to “SOCKS Host” enter “localhost” without the quotes followed by 8080 as the port.
- Save the settings.
If you need SSH tunnel protection outside of the browser, check each piece of software you use for custom proxy settings, then enter the same details as above.
Other Methods of Unlocking the Internet
Encryption isn’t restricted to VPNs or SSH tunnels. There are several other popular methods used to break through censorship firewalls or defeat anti-neutrality measures put into place by ISPs.
Shadowsocks (SOCKS5 Proxy)
Shadowsocks was made to restore open internet access in places like China. It uses the SOCKS5 protocol (Socket Secure 5) which transfers encrypted data packets between clients and servers by using a proxy server, masking the details of the source and destination in the process. SOCKS also provides a layer of authentication to make sure only the intended parties can access the information, making it even more difficult for ISPs to snoop through your data.
Shadowsocks is a little easier to use than other methods, but it does require some extra steps. For starters, you’ll need access to a shadowsocks server which requires deploying your own or renting one from an external service. It’s cross-platform, completely open source, and straightforward to use once you begin, however, making it a viable alternative if net neutrality is destroyed.
SSL/TLS Tunnel
SSL (Secure Socket Layer) tunnels are used every day by most people on the internet. Have you ever seen that little green icon in your browser window that shows up when connecting to an HTTPS site? That’s SSL doing its thing. SSL traffic is common, surprisingly fast, and moderately secure. This makes it an amazing alternative to VPNs and other tunnels in areas wrought with censorship or anti-neutrality policies.
SSL tunnels wrap traffic in its own style of encryption and sends it through a non-standard traffic port. Since websites commonly use these methods for transmitting data, ISPs or censorship firewalls won’t notice anything unusual. To use an SSL tunnel you’ll need to download the stunnel software, which is a bit of a pain to install and use. Once you learn the ins and outs of the app, though, you’ll be able to enjoy the open internet once again.
Tor and Onion
You’ve probably heard of the Tor Browser and its powerful anonymizing features. The software leverages the Tor network which uses a series of distributed, decentralized computers to pass data from one node to another. It does this using onion routing, a process of wrapping packets of data in multiple layers of encryption. Each node peels away a single layer of encryption before sending it to the next computer on the network. At the end, the packet is processed normally, then sent back to the origin via the same network.
Tor really is an amazing tool for adding anonymity to daily internet activities. Its incredibly slow nature makes it a poor choice for things like large file downloads and video streams, however. Tor is also pretty easy to block and will likely be one of the first tools to disappear if net neutrality is killed.
RELATED READING: How to Use Tor with a VPN
Obfsproxy
Obfsproxy, which is short for obfuscation proxy, is a tool that helps circumvent censorship and internet control methods by hiding OpenVPN or SSH traffic under an additional envelope of encryption. The process is extremely complex and difficult to pull off for casual users, however, making it a poor choice for basic unblocking actions.
Comparison of the Best VPNs for Unlocking the Internet with SSH Tunneling
- 24/7 Live Chat
- 24/7 Live Chat
- 24/7 Live Chat
- Netflix,
- Disney+,
- Amazon Prime,
- iPlayer,
- YouTube,
- Hulu
- Netflix,
- Disney+,
- Amazon Prime,
- iPlayer,
- YouTube,
- Hulu
- Netflix,
- Disney+,
- Amazon Prime,
- iPlayer
Best VPNs for Unlocking the Internet
Defeating tiered internet packages and censorship firewalls is never an easy task. SSH tunnels make incredible strides in that direction, but they’re not perfect. VPNs fill in most of the gaps left by SSH tunnels and are superior in just about every way. By choosing the right VPN you can preserve many of your online freedoms without going through complicated set-ups.
Picking a good VPN with additional encryption support isn’t a straightforward process. In fact, most mainstream VPNs don’t offer anything beyond the standard OpenVPN protocol. There are a few that go above and beyond the norm, though, which is why we’re recommending them to anybody interested in keeping their data private and their internet connections unmonitored.
1. NordVPN
- Very fast speeds make this a strong choice for 4K streaming
- Over 5,400 servers in 61 countries
- Strong security features
- Based in Panama
- Money back guarantee policy
- Apps can sometime be slow to connect
NordVPN is the best all-around VPN provider. The service’s huge network of over 5,100 servers in ~60 different countries is one of its biggest selling points, but the thorough zero-logging policy that covers everything from traffic to bandwidth, IP addresses, and even time stamps is also worth mentioning. Users enjoy features like DNS leak protection, an automatic kill switch, and 256-bit AES encryption on every connection through every device, as well.
NordVPN doesn’t offer SSH tunnel support, but it does deliver obfsproxy and SSL tunnels through its main apps. Both methods help secure your connection using additional encryption measures and are great options to have as back-ups in case net neutrality goes out the window.
Read our full NordVPN review.
2. Surfshark
- Very fast speeds make this a strong choice for 4K streaming
- Over 5,400 servers in 61 countries
- Strong security features
- Based in Panama
- Money back guarantee policy
- Apps can sometime be slow to connect
While SSH tunnels have been used for years to beat site blocks, there are now plenty of modernized alternatives. Surfshark is one of the freshest faces in the room of top-tier VPNs, but it’s already established itself among the industry’s best. It brings with it a plethora of technological and quality of life updates that are fast becoming viewed as indispensable, rather than extra.
For one, Surfshark has upgraded their encryption cipher to the same one used by the NSA: 256-AES-GCM. In practical terms, this is unbreakable, even with theoretical computing power. Moreover, they’ve done away with outdated tunneling protocols, favoring OpenVPN, IKEv2/IPSec, WireGuard, and Shadowsocks (Windows only) instead. This not only improves security, but performance as well.
And rather than restricting advanced features like obfuscation to a few specialty servers, every one of their 800+ nodes is capable of beating DPI and sneaking past VPN blocks. Coupled with an outstanding, independently verified no-logging policy, and it’s easy to see why Surfshark’s enjoyed such meteoric success.
3. ExpressVPN
- SPECIAL OFFER: 3 months free (49% off – link below)
- 3,000+ super fast servers
- No DNS/IP leaks found
- No logging policy well enforced
- Great support (24/7 chat)
- Power-users configuration options
ExpressVPN is one of the fastest VPNs on the market. The company’s large server network spans most of the globe to deliver quick connections no matter where you live, work, or travel. Default 256-bit AES encryption locks your data down nice and tight, while a zero-logging policy on traffic, DNS leak protection, and an automatic kill switch keep you secure above and beyond the norm. ExpressVPN’s apps are also incredibly easy to use. Want to stay safe online? Just fire up the software and click a button, that’s it!
ExpressVPN doesn’t support SSH tunnels by default. It does allow for SSL tunnels on its main apps, which provides similar obfuscation that will help defeat blocks and website censorship just as effectively.
Read our full ExpressVPN review.
Conclusion
The loss of net neutrality means a crippling of everyone’s online freedoms. Small businesses will suffer, innovation will see a sharp downturn, and daily internet use will be a remarkably different affair. VPNs can go a long way to restoring the normal internet, but even they have their drawbacks. Unique encryption methods like SSH tunneling require a little set-up and technical know how, but they’re perfect for defeating tough blockades imposed by ISPs. Got any tips about unlocking the open internet? Share your knowledge in the comments below!
If you need a VPN for a short while when traveling for example, you can get our top ranked VPN free of charge. NordVPN includes a 30-day money-back guarantee. You will need to pay for the subscription, that’s a fact, but it allows full access for 30 days and then you cancel for a full refund. Their no-questions-asked cancellation policy lives up to its name.


I love how you see all of the scum the Democrats are in, how everything they do and say is meant to lie to you and to give them more power. And so you still think that you can trust them with regulatory power over the internet.
It’s really simple. They can make laws as they are needed, not create regulatory authority. Remove the fascist left tech tyrants from their 230 protections, and then start telling ISPs that if they keep dictating what their customers are allowed to access, they’re going to lose those protections too.