How To Set Up Firejail On Linux
Linux has a reputation of being fairly secure, and out of the big three operating systems it runs into far less issues when it comes to privacy. Still, as secure as Linux can be, there’s always room for improvement. Introducing Firejail. It’s an application that allows users to take any running app, and “jail it”, or “sandbox it”. Firejail lets you isolate an app and prevent it from accessing anything else on the system. The app is the most popular program sandboxing tool on Linux. It is because of this, many Linux distributions have decided to ship this software. Here’s how to get the Firejail on Linux.
SPOILER ALERT: Scroll down and watch the video tutorial at the end of this article.
Installation
Ubuntu
sudo apt install firejail
Debian
sudo apt-get install firejail
Arch Linux
sudo pacman -S firejail
Not happy with the repo version of Firejail on Arch? Consider building the Git version from the AUR instead.
Fedora
Unfortunately, there is no Firejail package for Fedora to be seen. The main repos don’t have it, and there’s no reason to believe this will change. Fedora users can still install the software, with Copr.
Copr is very similar to PPAs on Ubuntu, or the Arch Linux AUR. Any user can make a Copr repo and put software on it. There are many FireJail Copr repos, so if the one we list in this article stops updating, feel free to go to the website and find a replacement.
To get Firejail on Fedora, do:
sudo dnf copr enable ssabchew/firejail sudo dnf install firejail
OpenSUSE
Like most third-party software for Suse, users will find Firejail in the OBS. Versions of Firejail can quickly be installed for the latest versions of Leap and Tumbleweed. Get them here.
Be sure to click the 1-click button to install via YaST.
Other
The source code for Firejail is readily available and easy to compile if you’re on an unsupported Linux distribution.
To start off, install the Git package on your version of Linux. Do this by opening your package manager, searching for “git” and installing it to the system. Be sure to also install any build tools special to your Linux distribution, if you haven’t already (it should be easy to find, just check your distro’s wiki). For example, compiling on Debian/Ubuntu requires build-essential.
Once the git package has been installed on the system, use it to grab the latest version of the Firejail software.
git clone https://github.com/netblue30/firejail.git
The code is on the system. Enter the downloaded folder to start the build process with the cd command.
cd firejail
Before this software can compile, you’ll need to run a configure. This will scan your PC, and tell the software what your PC has, what the specifications are, and etc. This is important, and without it, the software will not build.
configure
The program is configured for compilation. Now, let’s generate a makefile. A makefile has instructions for building a piece of software. Do this with the make command.
make
Lastly, install the firejail software to your system:
sudo make install-strip
Using Firejail
Sandboxing something with Firejail is easy. For a basic program sandbox, all that is required is to use the “firejail” prefix before entering a command. For example: to Sandbox the Gedit text editor, and silo if off of the rest of your Linux installation, you do: firejail gedit in the terminal. This is pretty much how it works. For simple sandboxing, this is enough. However, because of how finicky this software is, some configuration is needed.

For example: if you run firejail firefox, the Firefox browser will run in a locked sandbox, and nothing else on the system will be able to touch it. This is great for security. However, if you want to download an image to a directory, you may not be able to, as Firejail may have no access to every directory on your system and etc. As a result, you’ll need to go through and specifically list out where a sandbox CAN and CANNOT go on the system. Here’s how to do it:
Profile Whitelisting And Blacklisting
Blacklisting and whitelisting are a per-app thing. There isn’t any way to set global defaults for what jailed apps can access. Firejail has many configuration files already set up. They generate sane defaults with these configuration files, and as a result basic users won’t need to do any editing. Still, if you’re an advanced user, editing these types of files can be useful.
Open a terminal, and head over to /etc/firejail.
cd /etc/firejail
Use the LS command to view all of the contents of the directory, and use a pipe to make each page viewable. Press the enter key to move down the page.
Find the configuration file for your app, and keep note of it. In this, we’ll be continuing with the Firefox example.
ls | more
Open the Firefox firejail profile in the nano text editor.
sudo nano /etc/firejail/firefox.profile
As stated before, the Firejail app has sane defaults. This means the developers have gone through and set up defaults that should work for most users. For example: though the app is jailed, the ~/Downloads directory, and plugin directories on the system are available. To add more items to this whitelist, go to the section of the config file where everything is being whitelisted, and write your own rules.
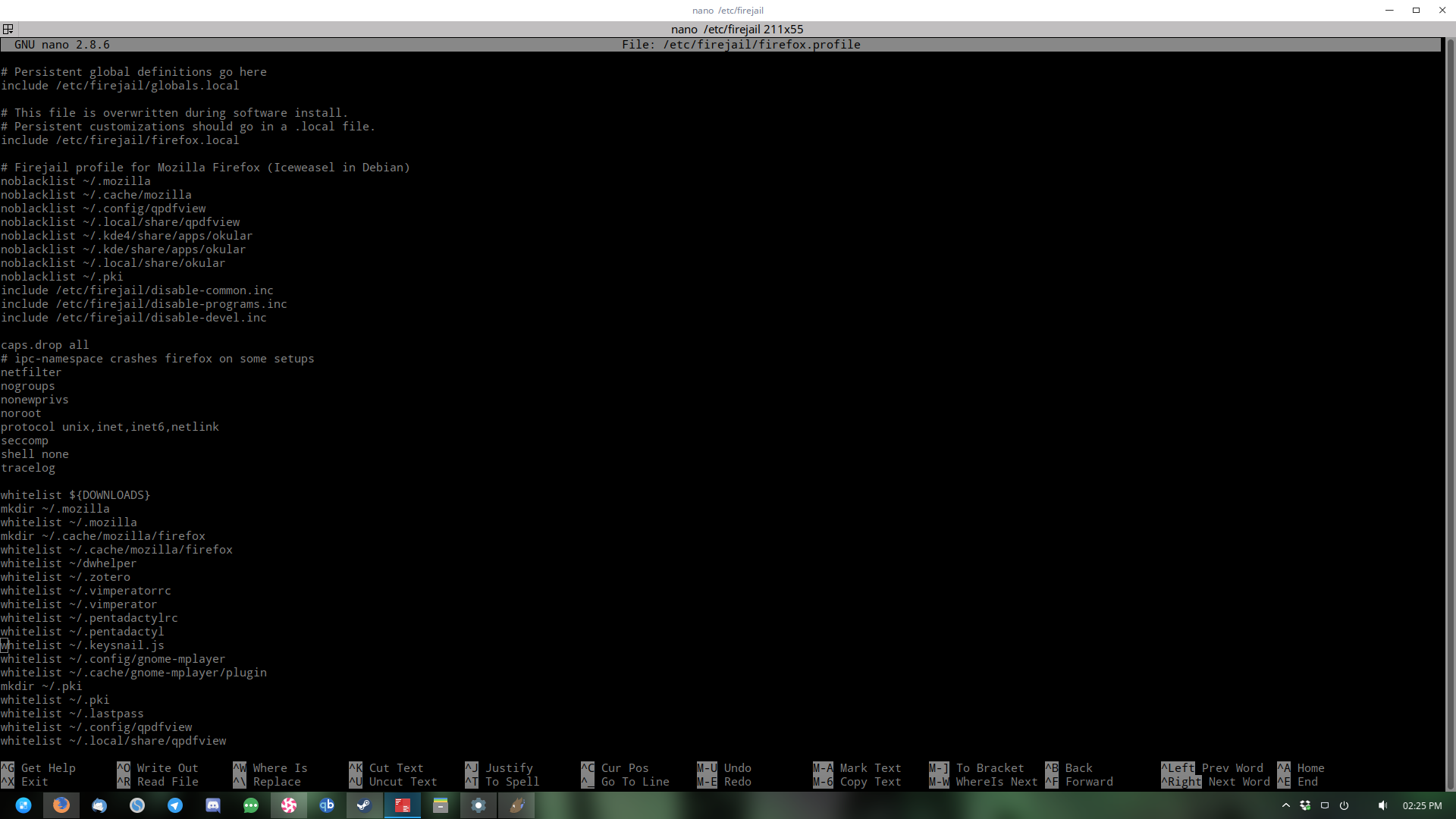
For example, to make it easier to upload photos to my Facebook profile in the firejail version of Firefox, I’ll need to add:
whitelist ~/Pictures
The same premise can be used for blacklisting. To prevent the sandboxed version of Firefox from seeing specific directories (no matter what), feel free to do something like:
blacklist ~/secret/file/area
Save your edits with Ctrl + O
Note: “~/” means /home/current user
Conclusion
Sanboxing is a brilliant way to safeguard yourself from leaky applications, or bad actors looking to steal your data. If you’re paranoid on Linux, it’s probably a good idea to give this tool a serious shot.

I very much wanted to upload a current copy of firejail, rather than relying on outdated software options through Linux Mint especially since the reviews given are negative. 3 of the 5 reviews were extremely negative, with 3 saying their computer crashed. However, updated versions are supposed to be better.
I’ve looked all over the internet, and the instructions are always for a command line install using sudo apt, and I think that this probably downloads the old version.
I cannot find an explanation that explains how to install and verify from Sourceforge a current copy – although I did find two people who did that but left out how to verify. On sourceforge, there is an asc. file and the .deb file, which took long enough to ID for me, but there just isn’t anything about how to verify after download.
Hey, just a heads up, Debian has been using apt install since at least Debian 8, if not Debian 7, and is now standard because of security problems with apt-get. You could probably merge those with no ill effects.