How to Secure A Linux Installation: The Basics
Linux is often touted as being the most “secure” operating system out of the big three. When it comes to Windows and Mac OS, Linux has the best security, they say. For the most part this is true, but not for the reasons most people might think. Security on Linux comes from obscurity. There just aren’t as many people using Linux, and as a result, there aren’t as many malicious people targeting it. If as many people used Linux as Windows 10, Linux users who claim that their operating system is the most secure would be proven wrong quickly. In this article, we’ll go over ways to secure a Linux installation.
Regardless of how secure something is or isn’t, there is one thing every Linux user needs to do: take control of their PC and make it harder for hackers to break into. We’ll go over how to create a strong password for Linux, how to configure the firewall, encryption and even scan for viruses.
Creating A Secure Password
The foundation of any good Linux installation is a solid password for both the root user, as well as any of the other users on the computer. This ensures that intruders have a hard time getting access to your PC. The best way to create a secure password is to understand what makes a good password.
There is a whole list of things to take into account when coming up with a good, secure password. However, this is time consuming. Instead, use this service: Strongpasswordgenerator.com. It’s a website that takes into account all the things that make a strong password, and generates one for you.
If you’re in the process of setting up a new Linux distribution — go to the password generation website during the setup process. Use your generated password inside the user setup process. If you’ve already installed your Linux distribution and wish to change user and root accounts to something more secure, follow the instructions below.
Strong password generator has a habit of generating really secure passwords that people sometimes forget. Be sure to write down your new password on a piece of paper and place it somewhere secure in your home.
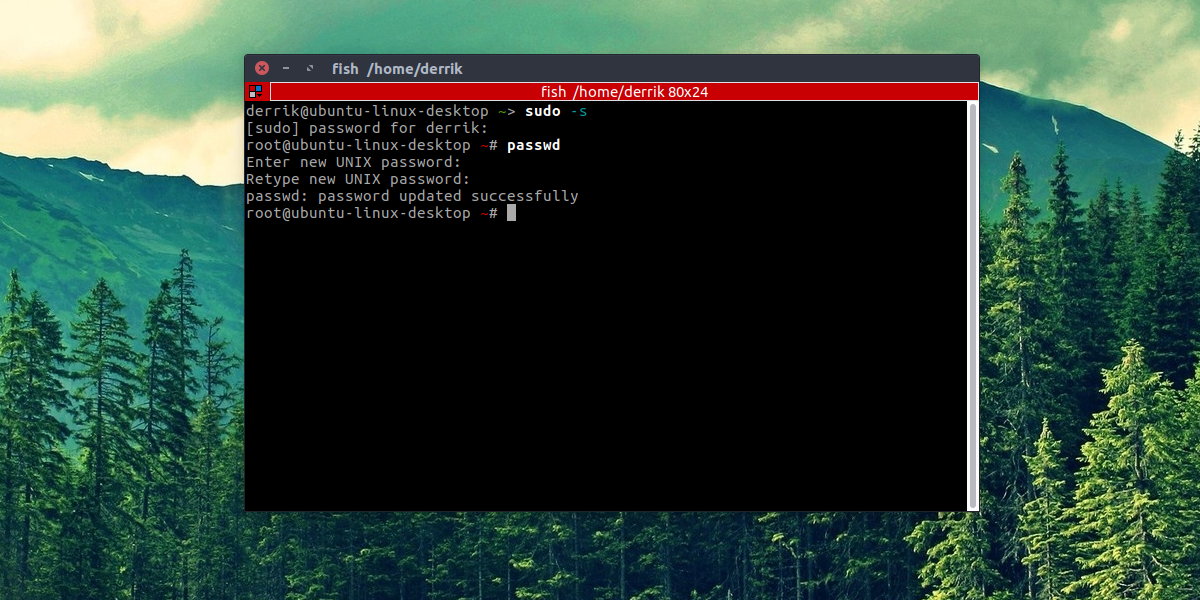
Change Passwords Of Existing Users
root
sudo -s
passwd
user
passwd username
Setting Up A Firewall
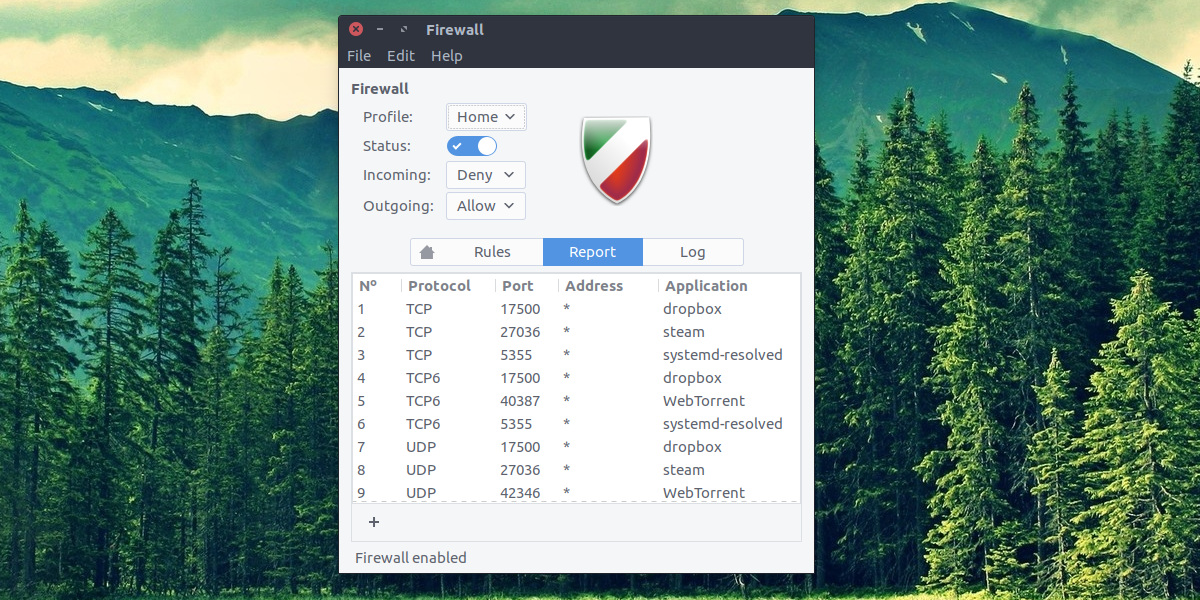
One of the best ways to secure a Linux installation is to take control of the network traffic that goes in and out. This is accomplished with a Firewall. Luckily, most mainstream Linux distributions (if not all) come with a pretty good firewall. Unfortunately, it’s usually turned off, or not configured securely enough. To configure the Linux firewall, we’ll first need to install a program.
This program is needed to make interacting with the Linux firewall much easier. Open a terminal and enter one of the listed commands below to install it. Alternatively, search the way you’d normally install software for a program called “GUFW”, and install it.
Ubuntu
sudo apt install gufw
Arch Linux
sudo pacman -S gufw
Fedora
sudo dnf install gufw
OpenSUSE
sudo zypper install gufw
Debian
sudo apt-get install gufw
GUFW gives the user total control of the Linux firewall. To turn it on, find “Status” and click the slider to turn it on. After that, look through the different firewall profiles and select one. These profiles are perfect, as they contain sane defaults. Developers of this program have taken into account what most people do with a firewall and configured it accordingly
Linux Antivirus
Contrary to popular belief, Linux does get malware, and it can get viruses too. It is certainly true that users of Linux are much less likely to be impacted by this. These days, however, attacks focusing on Linux users are becoming more and more of a real thing. Additionally, it’s good to have an antivirus tool to use simply due to the fact that Linux users can inadvertently pass along Windows viruses on networks.
The best virus tool for Linux is ClamTK. It’s an open source, graphical front-end to the very popular ClamAV command-line virus scanner for Linux. Here’s how to install it:
Ubuntu
sudo apt install clamtk
Arch Linux
sudo pacman -S clamtk
Fedora
sudo dnf install clamtk
OpenSUSE
sudo zypper install clamtk
Debian
sudo apt-get install clamtk
Other
ClamTK is very popular. As a result, it is everywhere. If your Linux distribution wasn’t mentioned, get it by searching for it where you normally install software.
Scanning For Threats
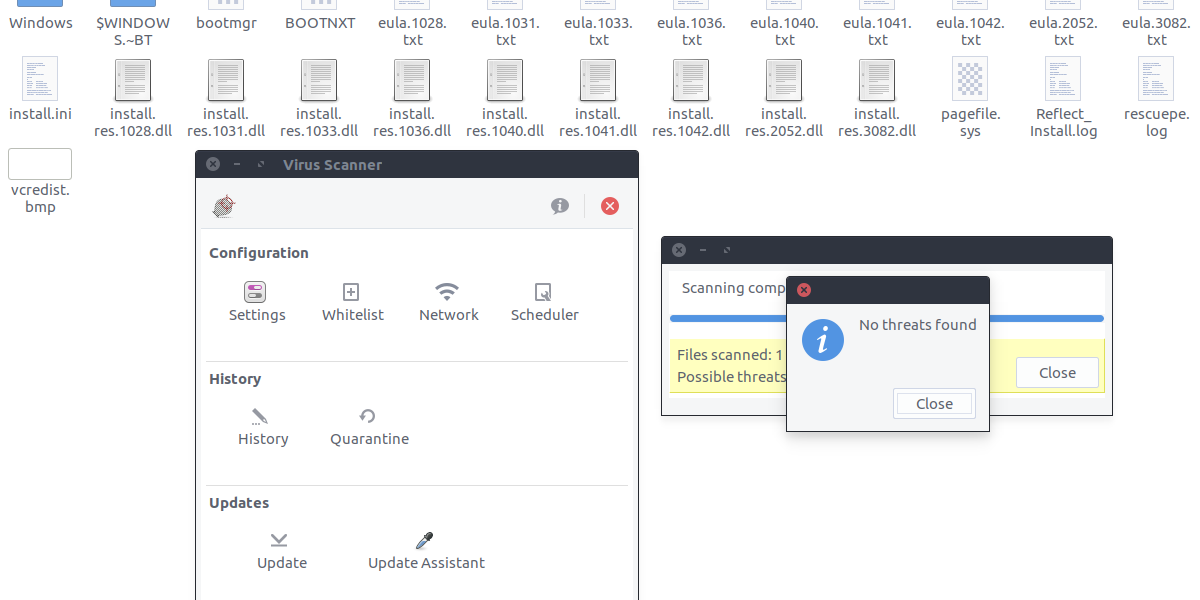
The virus scanner can easily identify threats by scanning individual files, or entire directories. To scan for threats, click either the “scan a file” or “scan a directory” button inside ClamTK. Then, use the file browser to look for what you’d like to check for vulnerabilities and threats. This could be a windows hard drive, partition or just files on a Linux PC.
Hiding Files And Folders
Part of protecting privacy and keeping secure on Linux is finding a way to keep sensitive documents away from prying eyes. Luckily, on Linux there is an easy way to hide sensitive documents, files and other things. To hide something, first open your file manager.
From here, find the folder or file you wish to hide, and press the F2 button on the keyboard (or right-click, rename) and put a period in front of everything. This means if you want to hide a folder called “Sensitive documents”, you’d rename it to be: “.Sensitive documents”. This goes for any type of file too.
This isn’t a perfect solution, but for those looking to hide away some sensitive information, this is a good option.
Encryption
All of the methods discussed in this article are great ways Linux users can take control of and secure a Linux installation. However, the single best way (besides a secure password) is opting for full-disk encryption during the installation process. Setting this up is very easy, as during installation, most Linux distributions have a little check-box to encrypt your entire hard drive.
If you’re a new Linux user and you’re looking to get full-disk encryption, Ubuntu is recommended. This is because it is the easiest to set up. Here are the instructions for Ubuntu.
Note: As mentioned before, pretty much all Linux distributions support full-disk encryption in one way or another. It is best to go to your Linux distribution’s website and search for instructions on encryptions. Alternatively, look through the setup tool for “encryption options” and etc.
This guide will not cover how to install Ubuntu Linux. Just the instructions for full disk encryption.
Boot up the Ubuntu live-disk like normal. This involves going through your PC’s BIOS options and setting it so that the USB disk will boot first. When Ubuntu finishes loading up, select “install Ubuntu”.
Check “Download updates while installing Ubuntu” and “Install third party software” options, then select the continue button to move onto the next page.
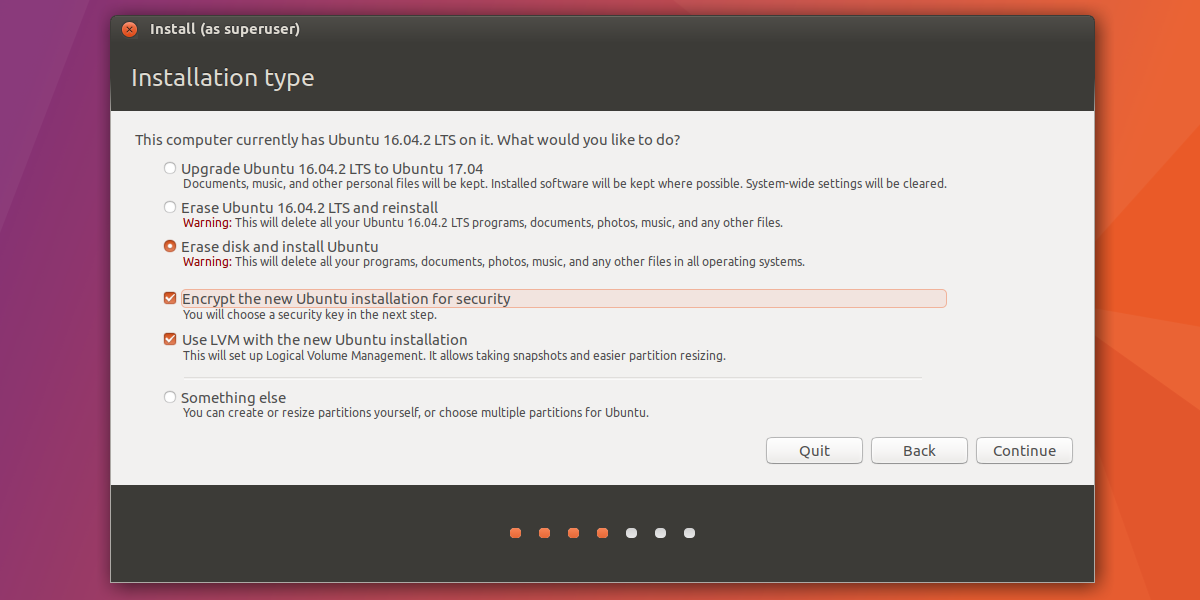
This next page is where full-disk encryption is set up. Select one of the options to install Ubuntu, and check the box labeled “Encrypt the new installation for security”, then click the continue button to set up the encryption key.
Be sure to use Strongpasswordgenerator.com to create your encryption key for maximum security.
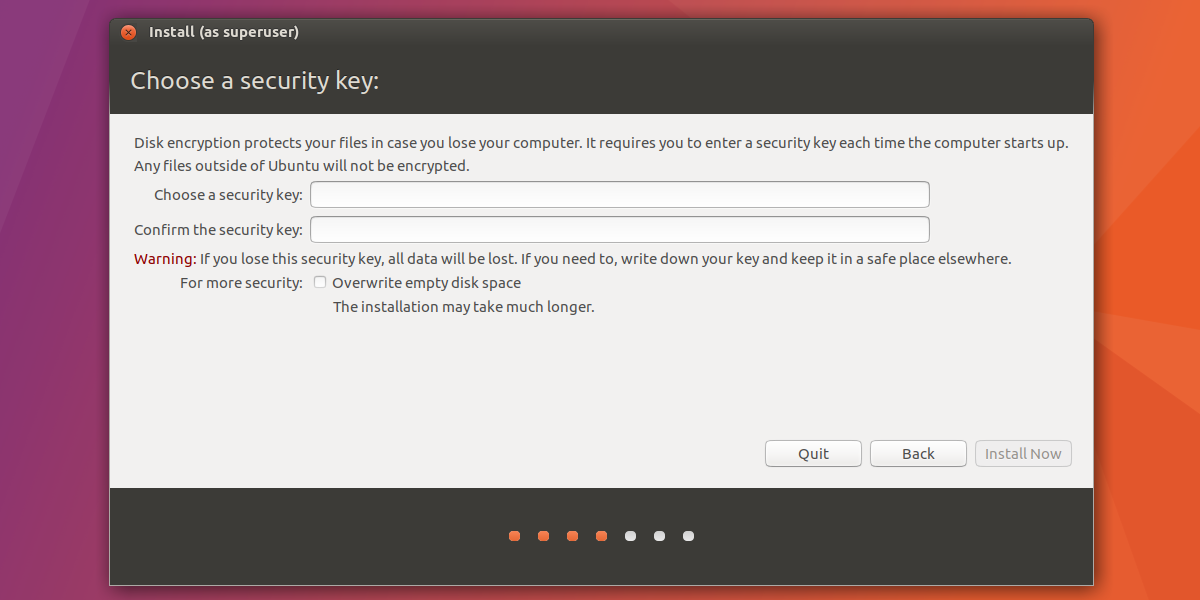
Once set up, click the continue button to move on with the installation of Ubuntu.
Conclusion
Linux has a bad reputation of being inherently secure. The reality is that no operating system, no matter what will ever be secure 100% of the time. The only way to keep your operating system secure and to prevent bad things from happening is to take precautions. Luckily, there are easy tools out there that make it so that even beginners can take control.