How To Enable Two Factor Authentication On Linux To Log In
Linux is known for requiring a password to do anything to the core system. It is because of this, many consider Linux to be a little more secure than most operating systems (though not perfect by any means). Having a strong password, and a good sudoer policy is great, but it’s not fool-proof, and sometimes it isn’t enough to protect you. That’s why many in the security field have taken to using two-factor authentication on Linux
In this article, we’ll go over how to enable two factor authentication on Linux using Google Authenticator.
Installation
Using Google Authenticator is possible, thanks to a pam plugin. Use this plugin with GDM (and other desktop managers that support it). Here’s how to install it on your Linux PC.
Note: Before setting up this plugin on your Linux PC, please go to the Google Play Store (or) Apple App Store and download Google Authenticator, as it’s a key part of this tutorial.
Ubuntu
sudo apt install libpam-google-authenticator
Debian
sudo apt-get install libpam-google-authenticator
Arch Linux
Arch Linux doesn’t support the pam Google authentication module by default. Users will instead need to grab and compile the module via an AUR package. Download the latest version of the PKGBUILD, or point your favorite AUR helper at it to get it working.
Fedora
sudo dnf install google-authenticator
OpenSUSE
sudo zypper install google-authenticator-libpam
Other Linuxes
The source code for the Linux version of Google Authenticator, as well as the libpam plugin used in this guide is readily available on Github. If you’re using a non-traditional Linux distribution, head over here and follow the instructions on the page. The instructions can help you compile it from source.
Set Up Google Authenticator On Linux
A configuration file needs editing before pam will work with the Google Authentication plugin. To modify this configuration file, open up a terminal window. Inside the terminal, run:
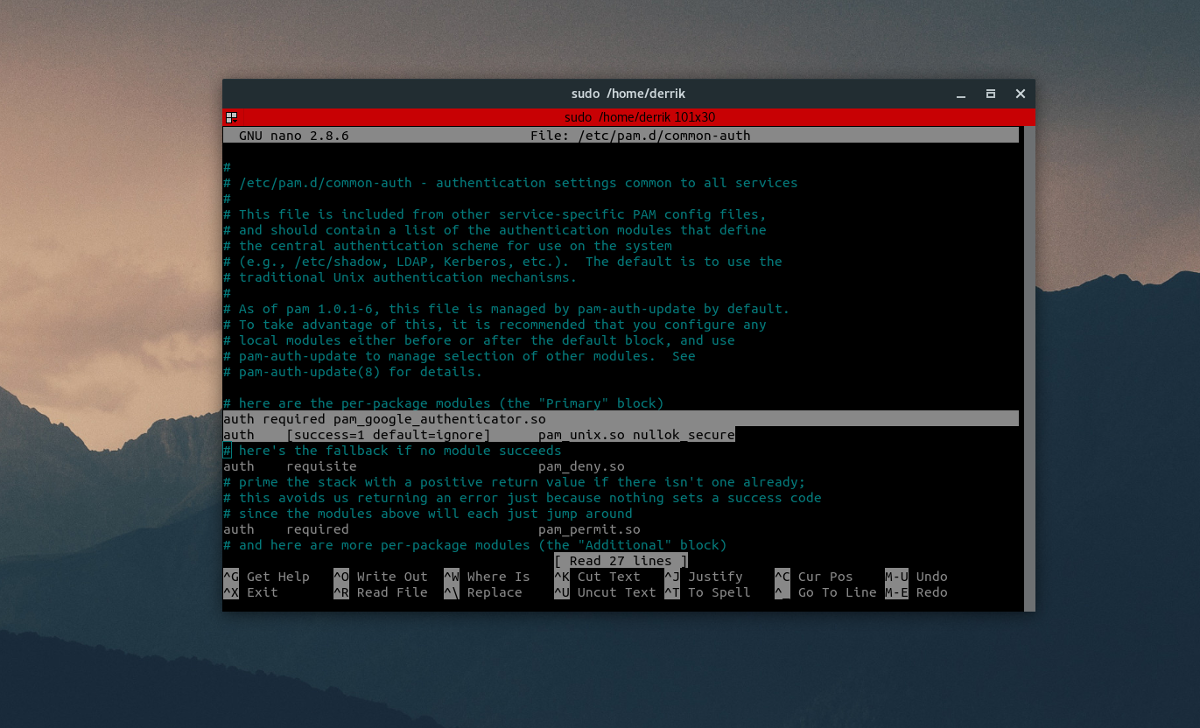
sudo nano /etc/pam.d/common-auth
Inside the common-auth file, there’s a lot to look at. Lots of comments, and notes for how the system should use authentication settings between services on Linux. Ignore all of this in the file, and scroll all the way down to “# here are the per-package modules (the “Primary” block)”. Move the cursor below it with the down arrow key, and press enter to make a new line. Then write this:
auth required pam_google_authenticator.so
After writing this new line out, press CTRL + O to save the edit. Then press CTRL + X to exit Nano.
Next, go back to the terminal, and type “google-authenticator”. You’ll then be asked to answer some questions.
The first question Google Authenticator asks is “Do you want authentication tokens to be time-based”. Answer “yes” by pressing y on the keyboard.
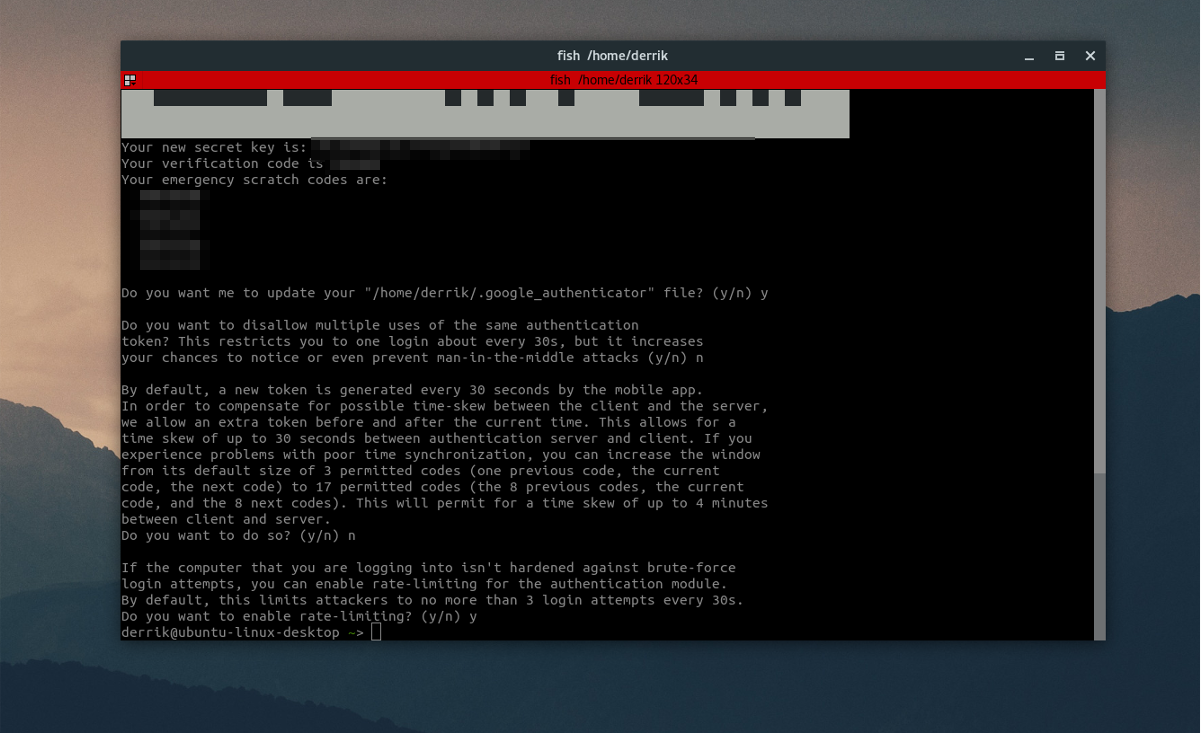
After answering this question, the tool will print out a new secret key, along with some emergency codes. Write these code down, as it’s important.
Continue on and answer the next three question as “yes”, followed by “no”and “no”.
The last question authenticator asks has to do with rate limiting. This setting when enabled makes it so that Google Authenticator will only allow 3 try/fail attempts every 30 seconds. For security reasons, we recommend you answer yes to this, but it’s perfectly OK to answer no if rate limiting isn’t something you care about.
Configuring Google Authenticator
The Linux side of things is working. Now it’s time to configure the Google Authenticator app so that it works with the new setup. To start, open the app and select the option “enter a provided key”. This brings up an “enter account details” area.
In this area, there are two things to fill out: the name of the PC you’re using authenticator with, as well as the secret key you wrote down earlier. Fill both of these out, and Google Authenticator will be operational.
Logging In
You’ve set up Google Authenticator on Linux, as well as your mobile device and everything works together as it should. To log in, select the user in GDM (or LightDM etc). Immediately after selecting the user, your operating system will ask for an authentication code. Open up your mobile device, go to Google Authenticator and enter the code that appears into the login manager.
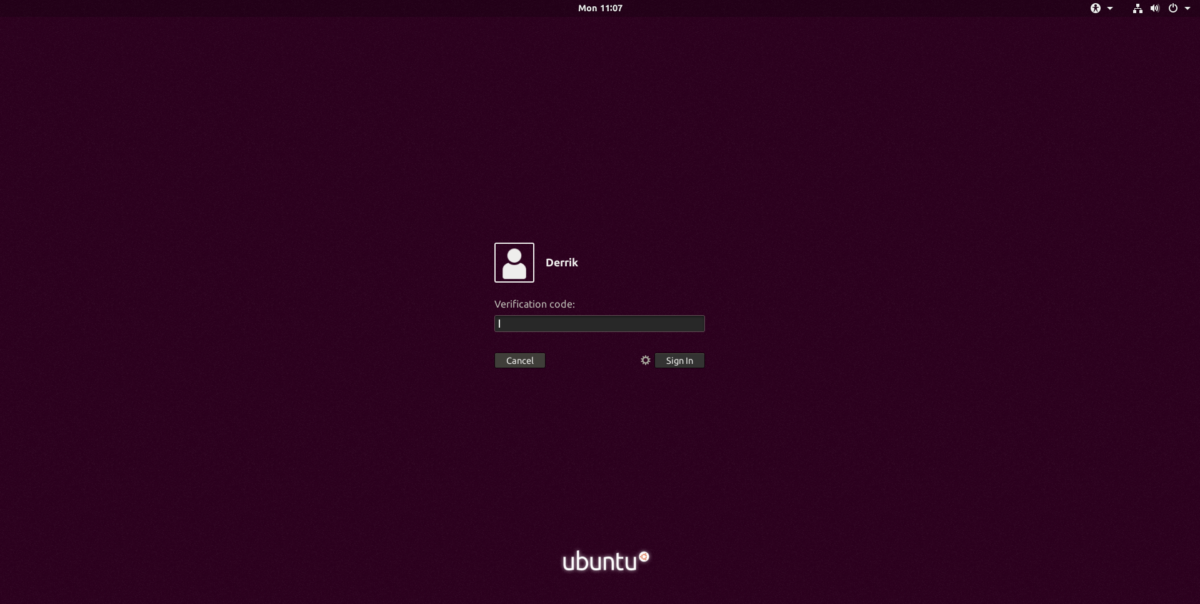
If the code is successful, you’ll then be able to enter the user’s passcode.
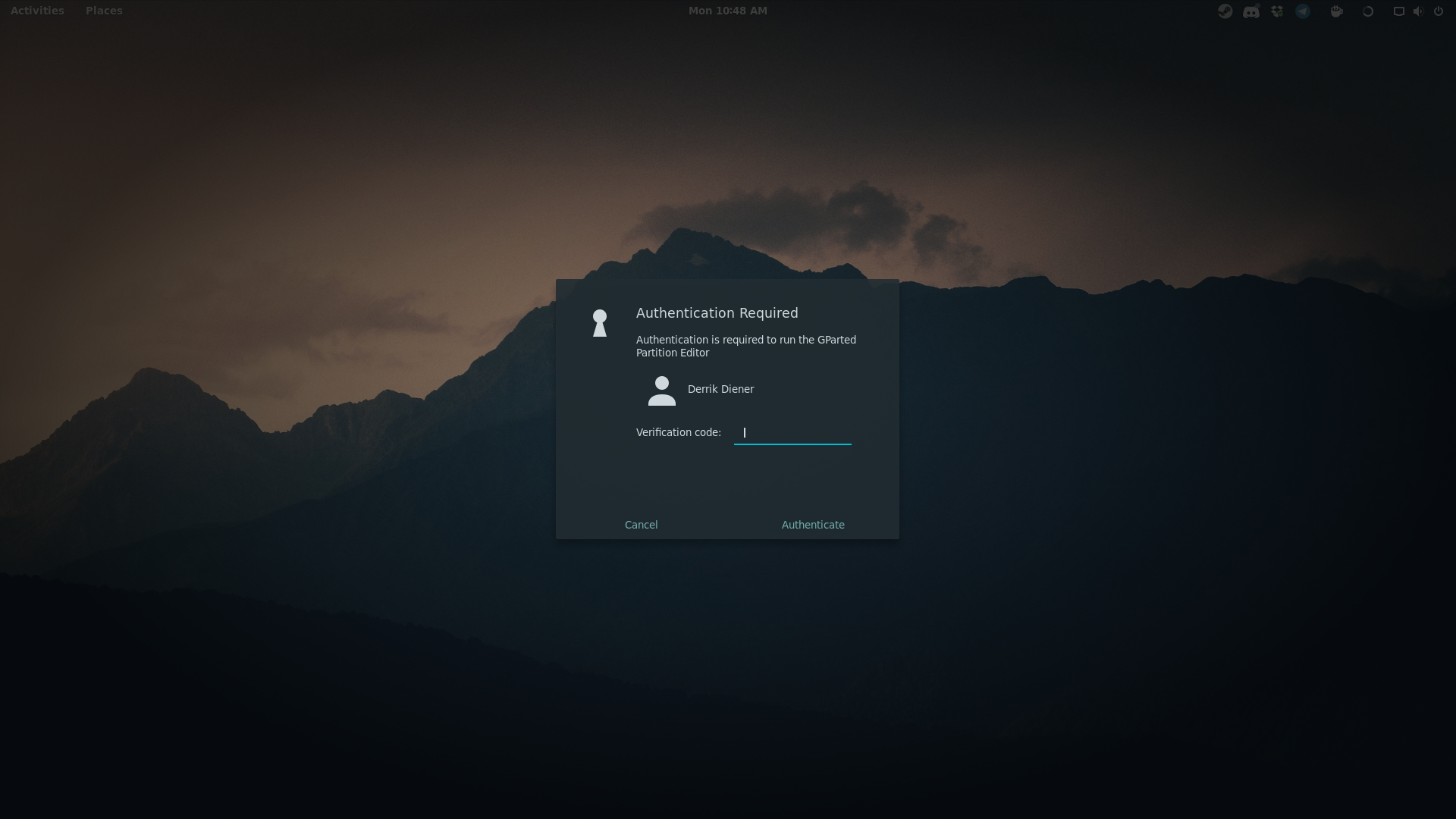
Note: setting up Google Authenticator on Linux doesn’t only effect the login manager. Instead, each time a user tries to gain root access, access sudo privileges, or do anything that requires a password, an authentication code is required.
Conclusion
Having two factor authentication directly connected to the Linux desktop adds an extra layer of security that should be there by default. With this enabled, it’s much harder to gain access to someone’s system.
Two factor can be iffy at times (like if you’re too slow for the authenticator), but all in all it’s a welcome addition to any Linux desktop manager.