Avoid Password Prompt When Executing The Sudo Command
If you have experience of working on the command line in Ubuntu then you are probably familiar with the sudo command, whenever you run the sudo command as a non root user then the system prompts you to enter the administrator’s password. This is a seriously annoying process.
Here is the simple tip which gets rid of this password prompt, follow these tweaks if you have a situation where you don’t want to enter the root password while running the sudo command as a non-root user.
You will need to modify a system file in this regard, so first open the terminal and run the following command to become the root user.
su
Once you are done, go through the following steps to get rid of this annoying password prompt for the sudo command.
- Assign the permissions to the sudoers file, by running the following command:
chmod 740 /etc/sudoers
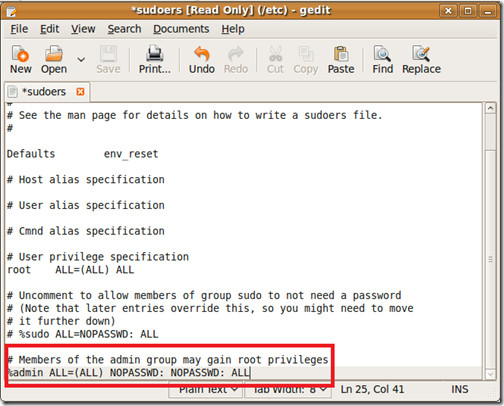
- Now edit the /etc/sudoers file and add the following line at the end of this file. (You can run gedit /etc/sudoers command to open the file for editing). Alternatively the best and secure way to edit the /etc/sudoers file is via visudo utility. You will need to run this utility from the command line, go to the /etc directory and run the command visudo. You will find the /etc/sudeors file opened. Add the lines as mentioned blow and then save the file by pressing ZZ or typing :wq! if you are in the command mode.
%admin ALL=(ALL) NOPASSWD: NOPASSWD: ALL
That’s it, now you will be able to run the sudo command as a non root user without being prompted to enter the password. It will literally save you time and increase productivity.
Update: Instead of using the Gedit to edit the sensitive sudeors file, we have included the visudo method which is more secure. Thanks to all commenters who pointed out the flaws.

Or just log in as root all the time….
Linux users are usually so stuck up on security they cannot see how implausible for something bad to happen is. Although, the biggest risk is probably the rm command. far, far more dangerous then any virus or hacker.
sudo -u oracle -H /bin/bash –login
oops… let me clarify. my question is if there is an alternative to “sudo -u oracle -i” other than “sudo su – oracle” (which seems to require root access)? The “sudo -u oracle -s” command works but that is not a full login shell and doesn’t source the oracle user’s environment. I have this setup:
%dbadmins ALL=(oracle) NOPASSWD: ALL
I also don’t think you can use that double “NOPASSWD: NOPASSWD:” in the file. When I try to enter that on RHEL4 while using visudo – it complains about a syntax error. That’s another good reason to use “visudo” – syntax checking.
I’m on RHEL4 so I don’t have the “sudo -i oracle” option to change to user oracle w/o a password, like “sudo su – oracle” … but I think that only works if the user also has the ability to sudo to root.
“su”? On Ubuntu?*giggle*
Just use sudo su.
I suggest everyone who read this to take a loot at http://blog.lynxworks.eu/20100102/ubuntu-spot-t…
I am a Linux Newbie, but from what i know about the Linux structure & its way of functioning: 'THIS IS A VERY DANGEROUS & RISKY TRICK'Rather this is the easiest way to compromise your Operating System & should be never done. A average user should use sudo only & only when extremely necessary.NEVER EVER USE THIS TRICK.If anyone doesn't like to type passwords he should use Windows & not Linux.
Poopieheads!
“This is a seriously annoying process.””It will literally save you time and increase productivity.”Are you a system administrator or an average desktop user? The former usually uses su instead of sudo and it's really not common for the latter to need administrative privileges as often as those two sentences suggest.
never, never, never, never, EVER edit /etc/sudoers with anything other than visudo!!!
Agreed. But if you want to disable it for a short period of time, then you can disable it and then later re-enable it.We do not recommend disabling it, but just wanted every linux user to know that this is possible.
I think it's a good article, although I would disagree doing so..But anyway it's a good-to-know for Linux users eh..
So much for 'bloggers' who understand the purpose of SuDu. Idiots.
Agreed. But if you want to disable it for a short period of time, then you can disable it and then later re-enable it.We do not recommend disabling it, but just wanted every linux user to know that this is possible.
I think it's a good article, although I would disagree doing so..But anyway it's a good-to-know for Linux users eh..
So much for 'bloggers' who understand the purpose of SuDu. Idiots.
I think it's a good article, although I would disagree doing so..But anyway it's a good-to-know for Linux users eh..
So much for 'bloggers' who understand the purpose of SuDu. Idiots.
Did you think the purpose of this post was to help people understand sudo? If so, your idiot comment might be more appropriately applied to yourself.
Isn't this a huge security risk?This basically nullifies any and all security built into linux. If everyone did this, there would be viruses for linux. There's a very good reason it asks for a password in the first place.
Agreed. But if you want to disable it for a short period of time, then you can disable it and then later re-enable it.We do not recommend disabling it, but just wanted every linux user to know that this is possible.
If it's a matter of convenience, wouldn't it make more sense to increase the password timeout than disabling completely? Ubuntu is installed with a default of 15 minutes and I rarely find myself having to enter the password more than once or twice while administering a system. And at times when convenience trumps security, I'll “root up” with sudo -i or su as was stated in the post above. There should be no reason to disable a security reason over convenience.