Use A USB Drive As Login Card For Windows
Securing your PC with a password that is long and contains alphameric characters is always a good technique. However, such passwords are quite difficult to remember, and when it comes to locking and unlocking your system frequently – while you go to get a coffee or lunch at work – it becomes quite tedious to enter the password over and over again. Previously, we covered a few alternatives to protect your computer from any unauthorized access including Blue Lock and Predator. The latter monitors a pre-configured USB flash drive and locks down the PC, in case it’s removed from the USB slot. Today, we have a similar application to share, which aims to make Windows Lock and unlock operations a breeze. Rohos Logon Key is an application that can turn your USB flash drive into a login card, eliminating the need for manually entering your user account password. Its user-interface isn’t filled with a plethora of options and is fairly easy to configure.
The application enables to use those jumbled up letters and yet you don’t need to remember them to login into your system. Moreover, it’s a much faster way to log in to Windows, and no one would get the slightest hint of the password. The application usage is quite simple, too. Simply connect your USB drive and launch the program. Click Setup USB Key to configure your USB flash drive. It must be noted that even after storing the password, all the user data on the flash drive remains intact and you may use it for data storage and transfer.
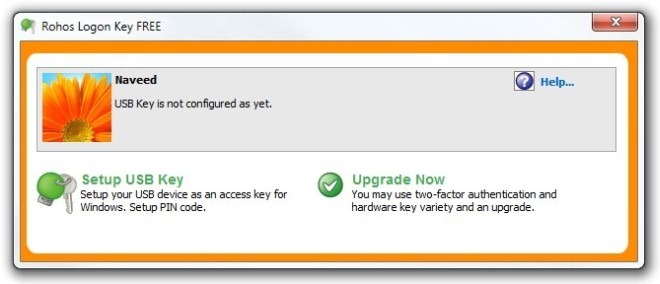
The application asks you to enter the user account password. Should you have connected multiple USB drives, click Change and select the appropriate one that you want to use. Upon entering the password, click Setup USB Key to complete the process.
The application stores and encrypts the password using AES – 256bit algorithm, and remains completely hidden. You may also Disable Key under the Setup USB Key window, which restores everything to default.
The application doesn’t use a master password to restore your account login password; adding it would have provided that extra layer of security.
Rohos Logon Key also offers a paid version, which costs $32 and features a few extra options, such as Secure 2-factor login, Emergency Logon etc. The application works on Windows XP, Windows Vista, Windows 7 and Windows 8. Testing was carried out on Windows 7 64-bit.

I like the concept of these, but they have always scared me because if you lose the USB drive, then you’ve got a problem. Sometimes these tools allow for the creation of backup USB drive copies; and sometimes a byte-for-byte USB drive copy created by another means will work. And other times there’s a special procedure for logging-in anyway, as long as you know such-and-such code or keystroke combination. It all just depends on the product.
But losing the key — or even having it go corrupt — oy! I dunno… it just seems too risky to me.
I feel the same way about drive encryption, by the way. It’s just too easy for there to be damaged clusters and all kinds of other crap that can turn an encrypted drive into a jumble of unusable crap. I’ve never encrypted a drive of which I had not first made a byte-for-byte, bare metal backup before encrypting. And I’ve never used an encrypted drive in day-to-day operation. Encrypting it before storing or transporting it, that’s different. That, I’ve done; but, even then, again, not before making an unencrypted bare metal copy of it first! In my 35+ years in IT, I’ve just seen too many things go wrong. No way would I ever trust encryption.
And so no way would I ever trust a USB key. If I could make copies, maybe; or if I could bypass the key with a special code or keystroke combination, maybe… but even then… I dunno. It just feels too risky.
For casual system protection, why not just use the BIOS-level password? I mean, okay, sure, a true hardware geek knows how to ultimately get around that; but for just plain ol’ everyday, casual system protection, why not just take the same position as one takes whenever one uses a standard doorknob or deadbolt lock on the door to one’s house? Of COURSE someone hell-bent on getting in could still get past them (hence the old joke that door locks are for honest people… people who will, upon see that the door’s locked, say to themselves that someone obviously doesn’t want just anyone to enter, so s/he, the honest person, will honor that and stop trying to enter), but for most everyday situations, a standard home doornob (and/or deadbolt) lock is good enough.
Why not, then, treat the BIOS-level password in much the same manner? It’s functional (ugly, but functional); and gets the job as done as most anyone would need for “everyday” casual purposes. No?
Just a thought.
The bottom line is that there really isn’t a foolproof method. Or, if there are foolproof methods, and if a USB key could be one of them, the potential downside (in this case, losing the USB key) is just too prohibitive… or so says at least me.
One time — you’re not gonna’ believe this — I was having this conversation with a client of mine, wherein I made the point that when it comes right down to it, the only chance anyone has of protecting a machine from unauthorized use is to protect the machine from being physically accessed. And so I made a suggestion about which I was serious in terms of my certainty of it working, but about which I wasn’t really serious because of its impracticality, to wit: I suggested that the best way to keep a machine from being physically accessed in a home, even if someone broke into said home, would be to buy a floor-standing gun/rifle safe… only one of the wider ones, like this one…
http://www.walmart.com/ip/Stack-On-Total-Defense-32-Gun-Fire-Resistant-and-Waterproof-Safe-with-Combo-Lock/14710124
…and then bold it to both the floor beneath it and the wall behind it; and then build a slide-out table sort of thingy with the computer and monitor and keyboard and stuff on it; and the printer beneath; and then, of course, always remember to turn the machine off, slide everything back inside, and close and lock the safe door whenever one was done using the machine.
To my astonishment, the client (for whom money was, obviously, no object) went home and did it. He was so eager to show it to me that he invited me and my wife over to his and his wife’s house for dinner so we could make an evening of it. I couldn’t believe it. He even went out of his way to get the wider one…
…which he didn’t buy from a discount store like Walmart. Rather, he got it from a gun safe store he found in a magazine, and which charged him about double the price that you see in the link to the Walmart safe, above. Yikes! That guy was a wildman… big-game hunter, with animal heads all over the walls of his home and office; filthy rich; a Republican, of course; and a big teller of tall stories. Still, ya’ couldn’t help but like him!
Anyway, it all makes the point that, in the end, it’s only the physical control of the machine, and not any software or hardware locking utilities, that has the highest statistical probability of actually and effectively stopping unauthorized use of said machine. My wacky client was simply willing to take it to a pretty much absurd (but nevertheless arguably nearly foolproof) extreme!
Hope that helps (or at least entertains). [grin]
___________________________
Gregg L. DesElms
Napa, California USA
gregg at greggdeselms dot com
Rohos Logon Key protect your computer even in Save Mode. 🙂
So if I lose the key or somebody steals it they can logon as me, or am I missing something?
yes, practically the same way if you loose your house keys or RFID pass anyone has access.