NetStalker Is A Rule-Based Firewall For Easy Internet Monitoring & Filtering
A lot of the applications we use nowadays have something to do with the internet in one way or the other. For instance, Dropbox requires constant internet connectivity to sync files between your local Dropbox folder to the one on the cloud, apps like Google Talk need internet connectivity to let you communicate with others, and even tools for offline use need internet access every now and then to update their data. In the most severe cases however, a malicious program sitting in some deep corner of your PC might be silently sending confidential information to someone, without you even knowing. This is where SterJo NetStalker comes to the rescue. This simple application acts as a firewall between your PC and the internet to keep an eye on all TCP and UDP connection established by currently running services and applications. It’s designed to constantly monitor your network traffic, and lets you block any processes from Internet access by creating rule-based policies.
Upon launch, the application automatically scans all currently running processes and services, and list them under the Activity tab, along with relevant information such as the connection protocol, local and remote IP addresses and port utilized by the connection, and the current status of the service (unknown, listening, established or close_wait). There’s also a status bar at the bottom that informs you about the activity of each of these connections such as the amount of bytes being sent or received, bandwidth speed, monitoring state and so on.
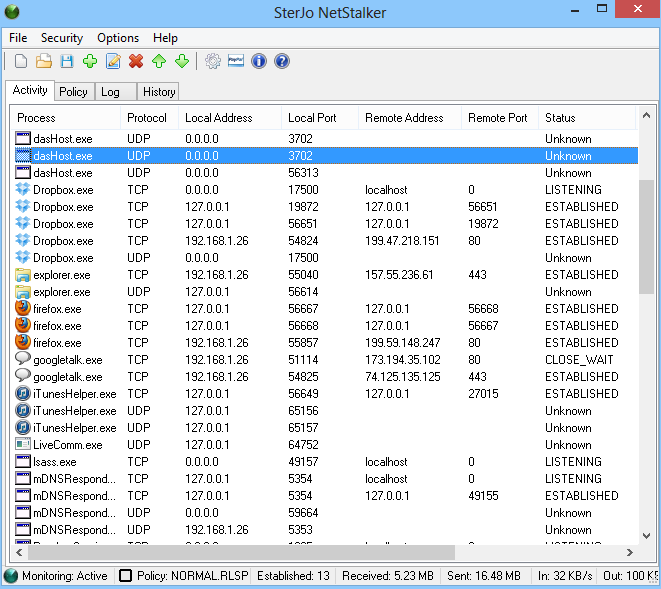
If the application encounters any suspicious or unauthorized process accessing the internet, it instantly informs you about it via a small pop up window, from where you can kill the process, or simply add it to the trust list if you want to allow it to access the internet.
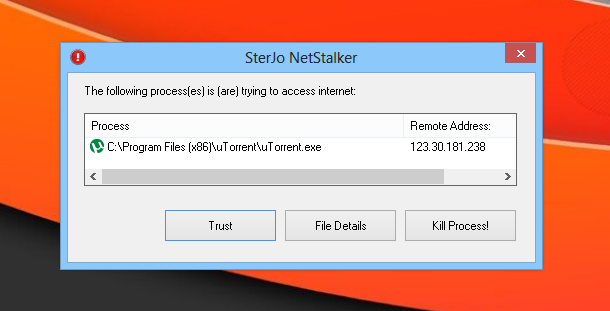
If a process doesn’t meet your defined network rules, it is quickly blocked by NetStalker and you’re informed of it through the bubble notification near the system tray.
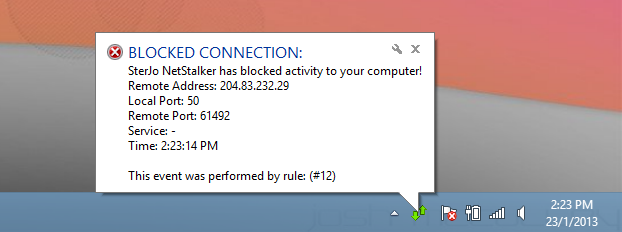
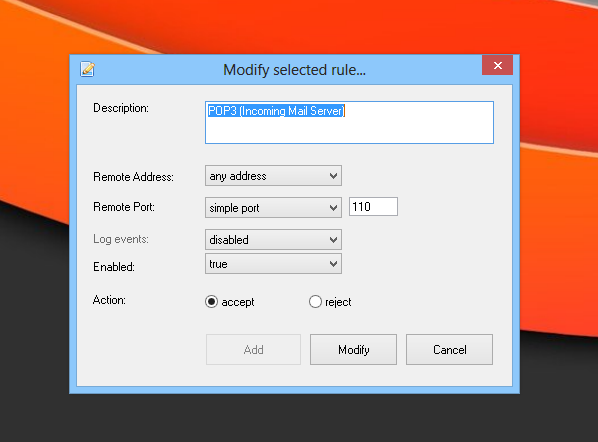
So how do the network rules actually work? These rules are based on simple Accept or Reject actions. To configure the rules, go to the Policy tab and right-click anywhere in this section. You can add new rules using the ‘Add a New Rule’ option of the context menu. SterJo NetStalker contains some pre-configured policies for HTTPS, SMTP, POP3, IMAP, FTP connections etc to help you get started. You can enable or disable these rules or policies on the fly from their right-click context menus.
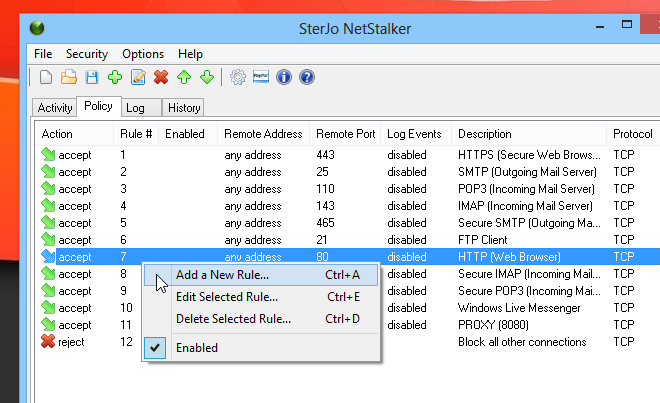
Both adding a new rule or modifying an existing one work pretty much in a similar fashion. You can specify a mini description for policy or rule, along with the remote address (IP), port, enabled state and action (accept or reject).
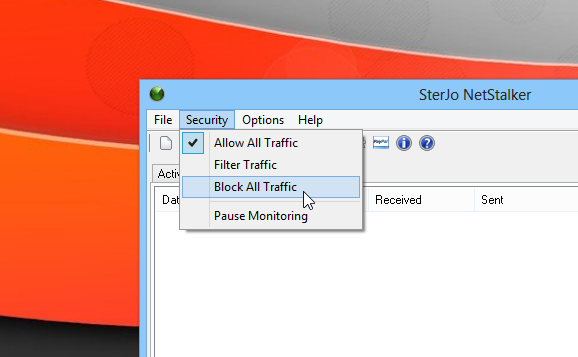
The Security menu allows you to change the current security mode of the application. You can specify whether to allow all traffic, filter traffic (as per the rules discussed above), or block all traffic. In addition, you can entirely pause the network monitoring as well. Lastly, the application also creates logs files of all its activity to help you keep track of all the internet activity of your apps. The Log tab houses all the logs created by NetStalker. while the History tab lists all the actions taken by the user when prompted by the app.
SterJo NetStalker works on both 32-bit and 64-bit editions of Windows XP, Windows Vista, Windows 7 and Windows 8.

Great software. Also a few more cool software could be downloaded from the developer’s web page.