How To Make An SSH Tunnel On Linux
When avoiding censorship online, most people are aware of “proxies” and VPN services. They’re tools that help users get around things like political censorship, or even just workplace IT rules. They’re also pretty great for those of us who are paranoid online and want an extra layer of privacy. For the most part, things like VPNs and even public proxy sites work very well. They’re easy to access and set up. For Linux users, there’s an easy way to get around silly network rules and quickly create some privacy when browsing online; make an SSH tunnel.
How Tunneling Works
Tunneling works by creating a “tube” or “tunnel” from the server host, to the client, effectively exporting the traffic from the host to the client. Effectively making it feel like you’re sitting right in front of the server, using its internet connection instead of the PC you’re on.
The tunnel is made possible by the Secure Shell Protocol: SSH. SSH tunneling doesn’t require a home server, of any kind. This is because running an SSH server is quite possibly one of the lightest programs around. Heck, you could even run it on a cell phone if you had the motivation.
Setting Up a Tunnel
It isn’t possible to SSH tunnel without an SSH server. Luckily, the setup process is quite easy. Start off by installing SSH and the server component. The command to install the components varies based on the operating system.
Ubuntu
sudo apt install openssh-server
Arch Linux
sudo pacman -S openssh sudo systemctl enable sshd sudo systemctl start sshd
Debian
sudo apt-get install openssh-server
Fedora/OpenSUSE
Fedora and OpenSUSE users will find that SSH is already on the system. Despite this, it may not be turned on. Turn it on via:
sudo systemctl enable sshd sudo systemctl start sshd
With the server installed, it’s time to tunnel.
SOCKS PROXY
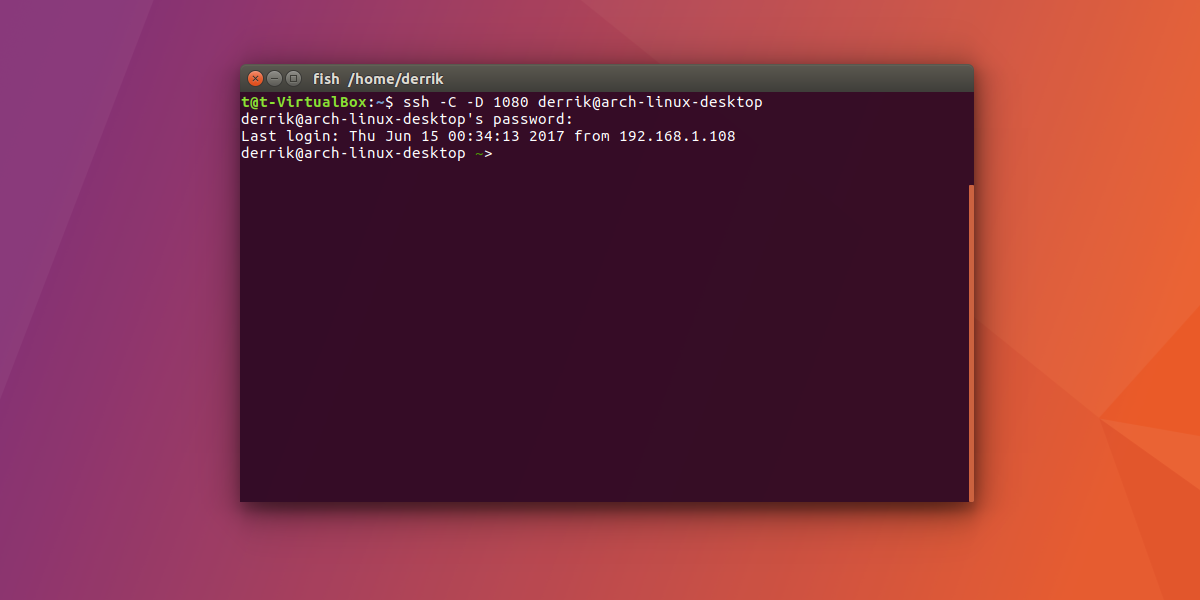
The best way to tunnel is the dynamic method. This ensures that the traffic stays secure. This is the best option to go with, for privacy reasons. Additionally, because the SSH tunnel is being turned into a SOCKS proxy connection, nobody will be able to eavesdrop on your connection.
ssh -C -D 1080 remote@ip-address
Keep in mind that you’ll need to change “remote@ip-address” with the username, and IP address of the PC you’re trying to send the tunnel to.
Configuring FireFox
Whichever type of tunnel you’d like to use, if what you want is to browse the internet, proxy settings need to be set up. Keep in mind that though SOCKS proxies work in all browsers pretty well, the best one to use is Firefox. This is because it has robust options.
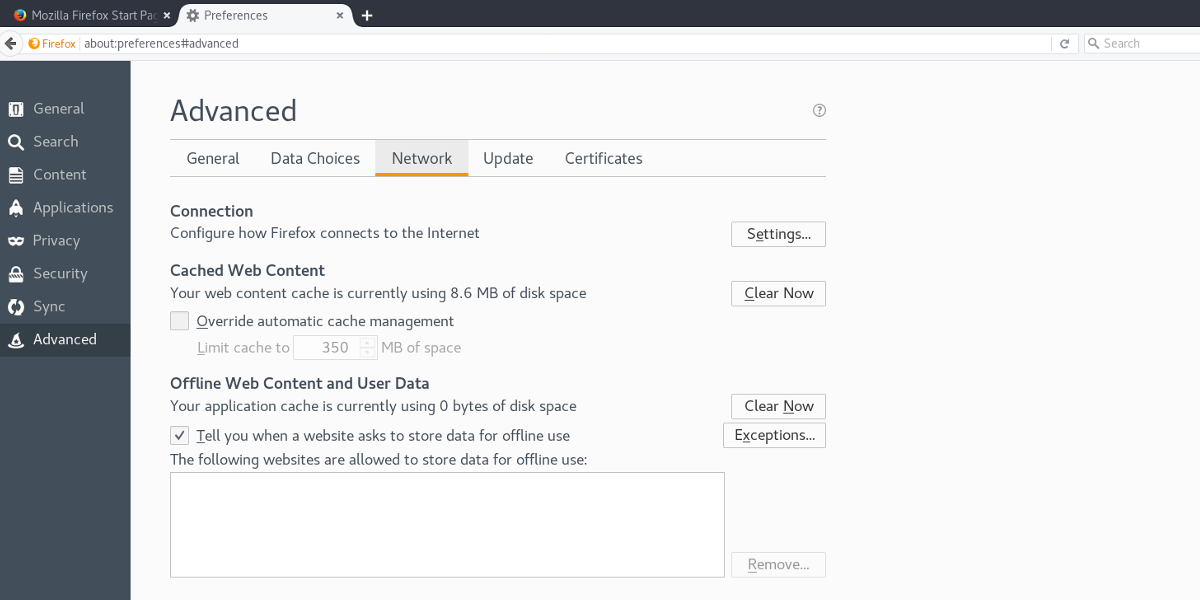
Start out by opening Firefox, then clicking the hamburger menu to reveal the settings area. Click “Preferences”, to bring up the preferences tab. Next, click “Advanced”, then “Network”.
Inside of the Network page, click “settings”, to reveal the proxy settings.
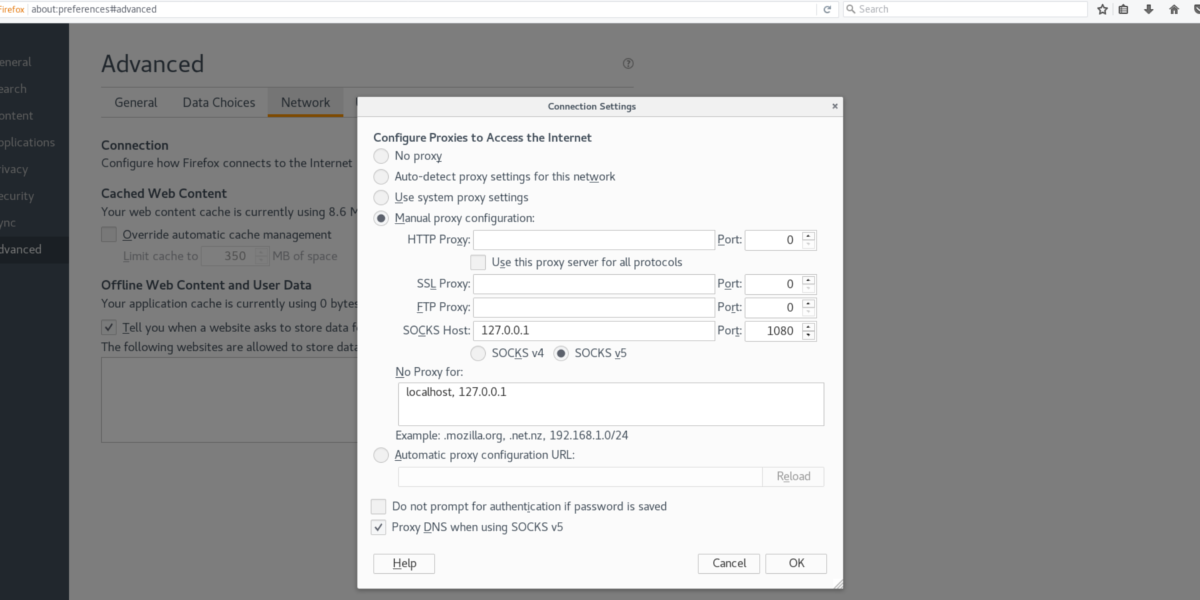
Find “Manual Configuration”, click the checkbox, and select the SOCKS HOST text area. In this text area for SOCKS HOST, put “127.0.0.1”. Use “8888” for the port. Then, click the OK button, open a new tab and enter “about:config” in the url bar.
Firefox About:Config
The about config area of Firefox is where advanced users can tweak and change up the internal workings of Firefox. For the SOCKS proxy to work, a setting needs to be changed, and nothing more.
On the about:config page, read the warning that shows up, and accept it to continue. Uncheck the checkmark box if you don’t want to see the warning again.
In the search bar, paste “network.proxy.socks_remote_dns”. Look for the option “False” and double-click on it so that it changes to true. After that, the SOCKS proxy will be working, and browsing can begin.
Note: When the SSH tunnel disconnects, the tunnel will go down. Additionally, if you’d like to use Firefox in normal mode, you’ll need to go back through the network settings, and change everything back to normal, or it will not work right.
Basic Local Tunnel
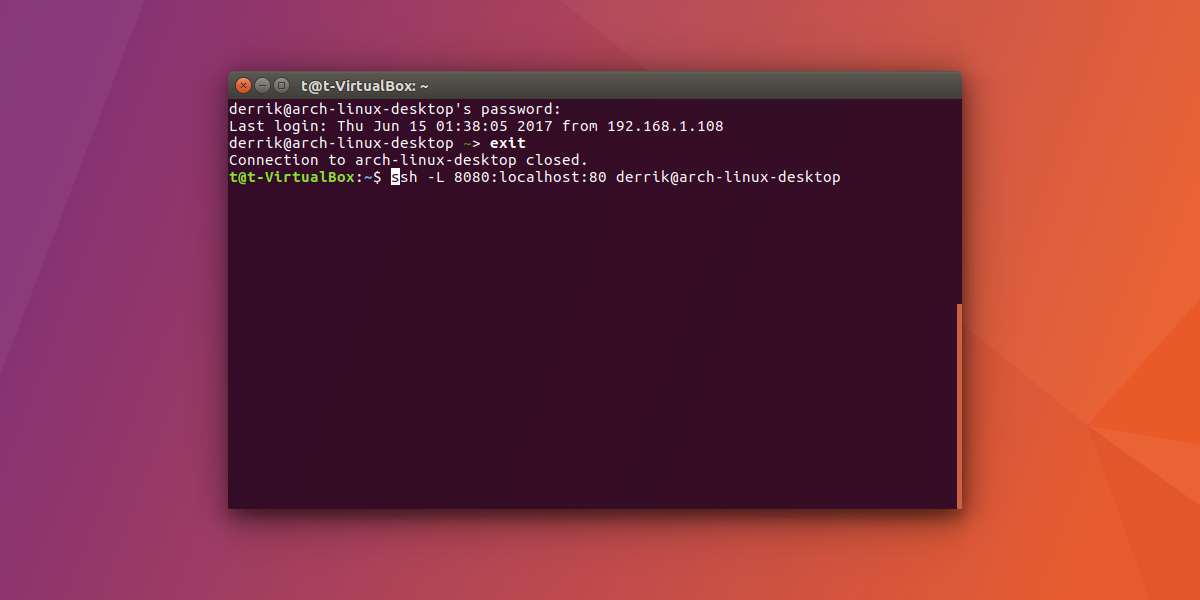
This is a tunnel that sends a connection locally to a remote connection. It is best when you want to connect the server with a remote PC. If you don’t need privacy, and you just want a remote connection via tunnel, use the local tunnel.
ssh -L 8888:localhost:80 remote@ip-address
Conclusion
Tunneling over SSH is a great way to direct internet traffic privately on demand. Additionally, it is a great option if you’d like to use a VPN but can’t afford it. This isn’t to say that using a VPN on Linux isn’t a great idea. However, there’s a time and place for them. If all you want is a quick way to direct traffic securely online with Linux, make an SSH tunnel.

And for a reason final result cannot be successful: In guide whose version history is Jun 16, 2017, suggested port number (8888) to be used by web browser is inadequate; the one specified in ssh command is 1080. Do not confuse such connection with a way to prevent DNF leaks from the ISP, which it is not. Indeed a test will reveal that client’s IP address and used DNS servers IP addresses are still the ones from the ISP.
Present guide tested on Linux newest QEMU/KVM virtualisation platform. Both Linux guests (server: 192.168.0.6/24 and client 192.168.0.7/24) have access to the internet via the same interface bridge networking to the host, and have the same static hostnames: localhost.localdomain.
A remote SSH connection from the client to the server is maintained in status established during the whole test. On client, highest available and selected SOCKS for Firefox is in v5. As final result, the proxy server is refusing connections.